CHaracter Aware Split Method
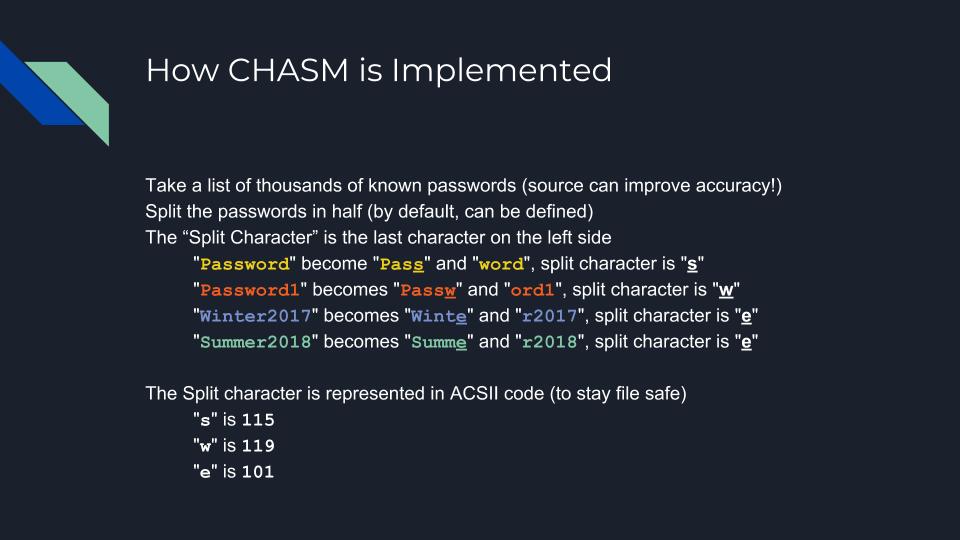
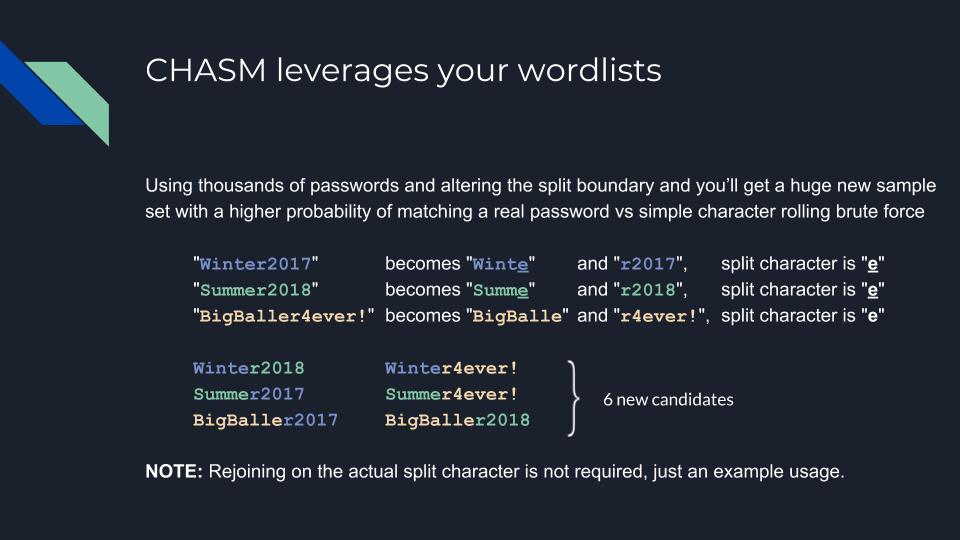
The main idea behind Chasm is to reuse password patterns in a way that is likely to produce probable password candidates.
- libjudy
On debian based systems use:
$ sudo apt install libjudy-dev
$ make
Or get the precompiled binaries.
They are statically linked against libjudy.
$ chasm -l 30 -k 2 out/chasm < dictionary.txt
- -a (Analyze frequency, will output the frequency of the split part)
- -c Create rules for dictionary attack eg left-side becomes prefix rules ^ conversely right-side becomes $ suffix rules
- -s Sort by frequency, highest first
- -o [charcode] Only splits if the split character matches the character code, eg -o 101 will only split on the letter 'e' at the defined midpoint/range
- -l [string len] Will not split if the length of the input string if greater than this number -l 20 will skip all strings greater than length 20.
- -k [min occurance] Will not write splits where occurrence is less than defined occurrence -k 2 will not output splits which only occur once
- -m [mid point] Instead of splitting the string in half (len/2) you can specify a position to perform the split on
- -r [number] Will split X chars around the middle including the middle, X denotes how far you want to branch out