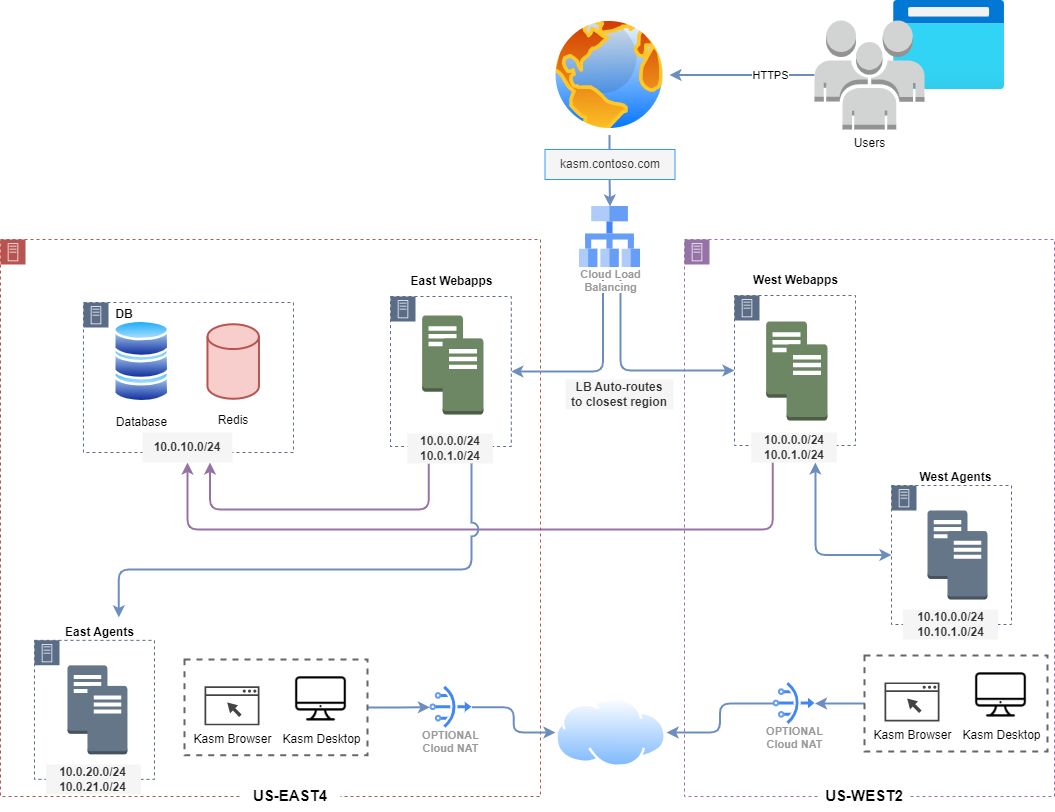
This project will deploy Kasm Workspaces in a multi-server deployment in GCP within multiple regions of your choice. Each Kasm server role is placed in a separate subnet and you can optionally forward traffic from user sessions on the Kasm Agent through a NAT Gateway.
NOTE: Make sure you read and understand the GCP requirements before continuing!
Consider creating a separate GCP Project for the Kasm deployment.
There are a couple of DNS options available with this GCP Terraform. Regardless of method, Terraform will:
- Add a DNS record for the load balancer
- Add a private DNS zone and add records for the private load balancer used by Agents to communicate with the webapps
-
Create and verify the public DNS zone before deploying Terraform - Using this method, you will create a DNS zone or use an existing DNS zone in the same GCP Project where you deploy Kasm
-
Allow Terraform to create the public DNS zone for you - Using this method, Terraform will create a public DNS zone using the values you provide, and you must manually add the name server (NS) records to the parent DNS zone so queries are forwarded correctly
Create a GCP Service Account to use with Terraform (https://cloud.google.com/iam/docs/service-accounts-create), and generate an API key. Once the API Key credential file is downloaded, copy it's contents into the gcp_credentials.json file in this directory, and Terraform will use these credentials to perform all operations.
Recommended Service Account roles:
- Compute Admin
- DNS Administrator
- Network Management Admin
- Service Account Admin
There are several GCP service APIs that must be enabled before this Terraform can build successfully. In your GCP project, navigate to each of these and ensure they are enabled before running the Terraform configuration stage below.
GCP APIs:
- Cloud DNS
- Cloud NAT
-
Initialize the project
terraform init -
Open
terraform.tfvarsand update the variable values. The variable definitions, descriptions, and validation expectations can be found in thevariables.tffile, or in the README.
In order to deploy this in multiple regions, simply add all additional regions in the
kasm_deployment_regionsvariable in theterraform.tfvarsfile. The first region in the list is where the Database will be deployed, thus, it is recommended to put this closest to those who will be responsible for Database administration to reduce network complexity and DB latency.
-
Verify the configuration
terraform plan -
Deploy
terraform apply -
Login to the Deployment as an Admin via the domain defined e.g
https://kasm.contoso.com
NOTE: The Load Balancer certificate can take between 15-45 min. to become active so you can access your Kasm deployment.
- Navigate to the Agents tab, and enable each Agent after it checks in. (May take a few minutes)