To authenticate you need to supply your INWX Username and Password.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| AuthUsername | AuthUsername is the INWX Username | string | true |
| AuthPassword | AuthPassword is the INWX Password | string | true |
Example:
provider, err := libdnsfactory.NewProvider("inwx", map[string]string{
"AuthUsername": "...",
"AuthPassword": "...",
})Repository: https://github.com/libdns/inwx
To authenticate you need to supply our AccessKeyId and AccessKeySecret to the Provider.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| AccKeyID | - | string | true |
| AccKeySecret | - | string | true |
| RegionID | - | string | false |
Example:
provider, err := libdnsfactory.NewProvider("alidns", map[string]string{
"AccKeyID": "...",
"AccKeySecret": "...",
"RegionID": "...",
})Repository: https://github.com/libdns/alidns
This package supports authentication using the Client Credentials (Azure AD Application ID and Secret) through azure-sdk-for-go.
You will need to create a service principal using Azure CLI or Azure Portal, and assign the DNS Zone Contributor role to the service principal for the DNS zones that you want to manage.
Then keep the following information to pass to the Provider struct fields for authentication:
TenantId(json:"tenant_id")- [Azure Active Directory] > [Properties] > [Tenant ID]
ClientId(json:"client_id")- [Azure Active Directory] > [App registrations] > Your Application > [Application ID]
ClientSecret(json:"client_secret")- [Azure Active Directory] > [App registrations] > Your Application > [Certificates & secrets] > [Client secrets] > [Value]
SubscriptionId(json:"subscription_id")- [DNS zones] > Your Zone > [Subscription ID]
ResourceGroupName(json:"resource_group_name")- [DNS zones] > Your Zone > [Resource group]
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| TenantId | - | string | false |
| ClientId | - | string | false |
| ClientSecret | - | string | false |
| SubscriptionId | - | string | false |
| ResourceGroupName | - | string | false |
Example:
provider, err := libdnsfactory.NewProvider("azure", map[string]string{
"TenantId": "...",
"ClientId": "...",
"ClientSecret": "...",
"SubscriptionId": "...",
"ResourceGroupName": "...",
})Repository: https://github.com/libdns/azure
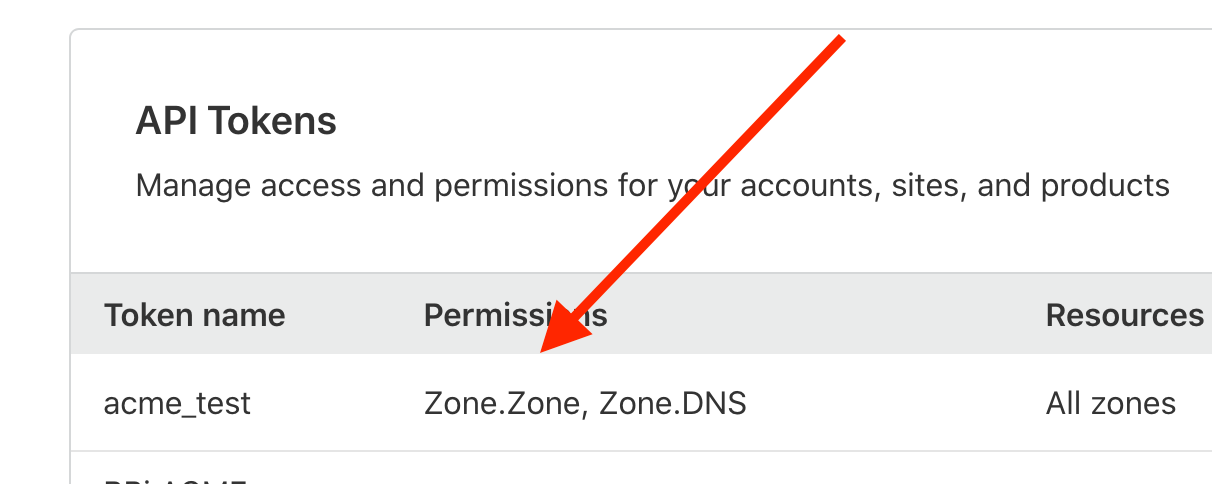
This package supports API token authentication.
You will need to create a token with the following permissions:
- Zone / Zone / Read
- Zone / DNS / Edit
The first permission is needed to get the zone ID, and the second permission is obviously necessary to edit the DNS records. If you're only using the GetRecords() method, you can change the second permission to Read to guarantee no changes will be made.
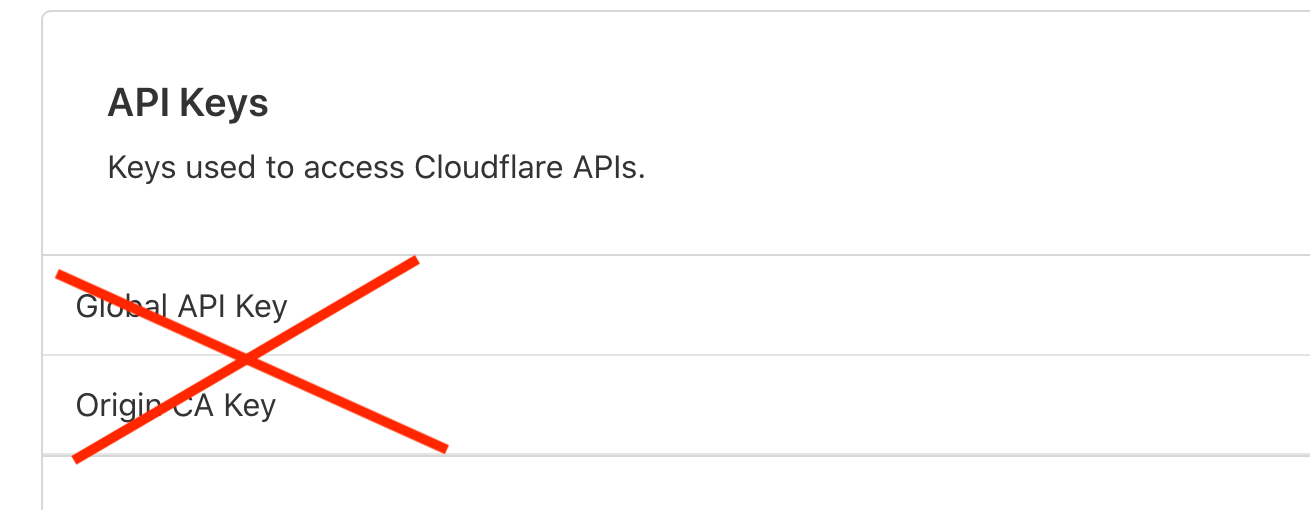
To clarify, do NOT use API keys, which are globally-scoped:
DO use scoped API tokens:
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| APIToken | API token is used for authentication. Make sure to use a scoped API token, NOT a global API key. It will need two permissions: Zone-Zone-Read and Zone-DNS-Edit, unless you are only using GetRecords(), in which casethe second can be changed to Read. |
string | false |
Example:
provider, err := libdnsfactory.NewProvider("cloudflare", map[string]string{
"APIToken": "...",
})Repository: https://github.com/libdns/cloudflare
To authenticate you need to supply a DigitalOcean API token.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| APIToken | APIToken is the DigitalOcean API token - see https://www.digitalocean.com/docs/apis-clis/api/create-personal-access-token/ | string | true |
Example:
provider, err := libdnsfactory.NewProvider("digitalocean", map[string]string{
"APIToken": "...",
})Repository: https://github.com/libdns/digitalocean
To authenticate you need to supply a DNSPOD API token.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| APIToken | APIToken is the DNSPOD API token - see https://www.dnspod.cn/docs/info.html#common-parameters | string | true |
Example:
provider, err := libdnsfactory.NewProvider("dnspod", map[string]string{
"APIToken": "...",
})Repository: https://github.com/libdns/dnspod
This package supports API Key authentication but does not yet support Sharing ID authentication. Refer to the LiveDNS documentation for more information.
Start by retrieving your API key from the Security section in Gandi account admin panel to be able to make authenticated requests to the API.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| APIToken | - | string | false |
Example:
provider, err := libdnsfactory.NewProvider("gandi", map[string]string{
"APIToken": "...",
})Repository: https://github.com/libdns/gandi
To authenticate you need to supply a Hetzner Auth-API-Token.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| AuthAPIToken | AuthAPIToken is the Hetzner Auth API token - see https://dns.hetzner.com/api-docs#section/Authentication/Auth-API-Token | string | true |
Example:
provider, err := libdnsfactory.NewProvider("hetzner", map[string]string{
"AuthAPIToken": "...",
})Repository: https://github.com/libdns/hetzner
This package supports all the credential configuration methods described in the AWS Developer Guide, such as Environment Variables, EC2 Instance Profile and the AWS Credentials file located in .aws/credentials. You may also pass in static credentials directly (or via caddy's configuration).
The following IAM policy is a minimal working example to give libdns permissions to manage DNS records:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Action": [
"route53:ListResourceRecordSets",
"route53:GetChange",
"route53:ChangeResourceRecordSets"
],
"Resource": [
"arn:aws:route53:::hostedzone/ZABCD1EFGHIL",
"arn:aws:route53:::change/*"
]
},
{
"Sid": "",
"Effect": "Allow",
"Action": [
"route53:ListHostedZonesByName",
"route53:ListHostedZones"
],
"Resource": "*"
}
]
}Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| MaxRetries | - | int | false |
| AWSProfile | - | string | false |
| AccessKeyId | - | string | false |
| SecretAccessKey | - | string | false |
Example:
provider, err := libdnsfactory.NewProvider("route53", map[string]string{
"MaxRetries": "...",
"AWSProfile": "...",
"AccessKeyId": "...",
"SecretAccessKey": "...",
})Repository: https://github.com/libdns/route53
To authenticate you need to supply our AccountName and the path to your private key file to the Provider.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| AccountName | - | string | true |
| PrivateKeyPath | - | string | true |
Example:
provider, err := libdnsfactory.NewProvider("transip", map[string]string{
"AccountName": "...",
"PrivateKeyPath": "...",
})Repository: https://github.com/libdns/transip
To authenticate you need to supply a Vultr API token.
Variables:
| Name | Description | Type | Required |
|---|---|---|---|
| APIToken | APIToken is the Vultr API token see https://my.vultr.com/settings/#settingsapi |
string | true |
Example:
provider, err := libdnsfactory.NewProvider("vultr", map[string]string{
"APIToken": "...",
})Repository: https://github.com/libdns/vultr