-
Notifications
You must be signed in to change notification settings - Fork 39
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Help: OIDC connection with keycloak #99
Comments
|
btw, is it normal to not have the host in this log : {"level":"info","ts":"2024-01-12T11:54:11Z","logger":"auth.oidc","msg":"checking request","host":"","path":"/cookbook","id":"5548994866080415820"} |
|
The |
|
Thank you, indeed, I make it works with the However, I think it does not follow this documentation : Normally the response from the Authorization Provider should go back through the Authorization Server. My understanding of the architecture diagram is that the AuthServer can protect multiple websites as it will receive the source host (which is currently empty into the log), perform the auth request and redirect the trafic to the source web site. Another point which is interesting, if I authenticate to https://my.website.com/ the authentication mechanism does not work, however if I try https://my.website.com/index.html it works. Last but no least, is there a way to get rid of the query param |
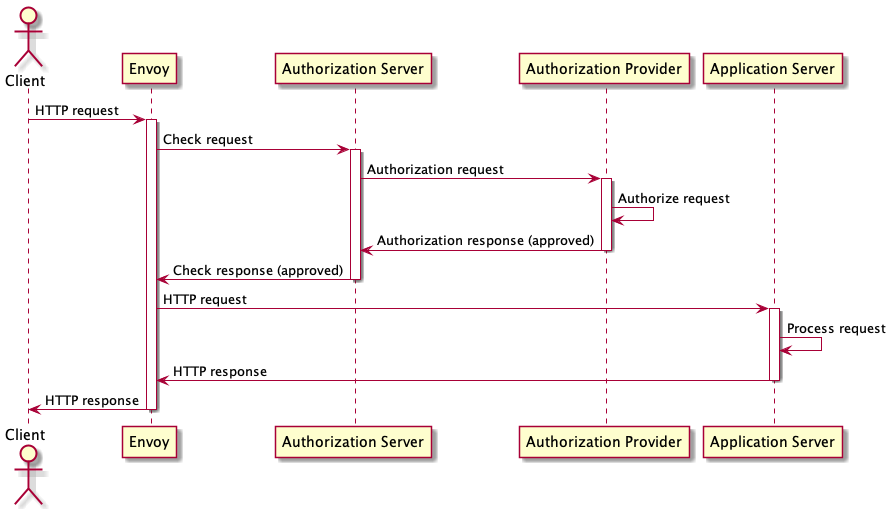
Hi there,
I am struggling to configure the contour-authserver to perform an OIDC connection with Keycloak.
When I access my website, envoy correctly root the trafic to contour-authserver to perform the authentication. Once the authentication is done, the connection is close and I do not access my web site.
In the redirectUri, I use the contour-authserver address targetting the port 9443 (but I feel this port only support gRPC request).
Should I configure the website url ? Is there another port which handle the http connection ?
Thank you in advance for the helm you may bring
The text was updated successfully, but these errors were encountered: