This vulnerability was discovered and disclosed by M. Akil Gündoğan from Secunnix Vulnerability Research Team. This repository will hold the proof-of concept and advisories.
- Product: SUPERAntiSpyware Professional X and all editions.
- Affected versions: <=10.0.1262 and lastest version 10.0.1264
- CVE ID: CVE-2024-27518
- Operating System: All supported Windows versions, tested on Windows 10 Pro
- State: Public responsible disclosure.
- Release Date: 03.04.2024
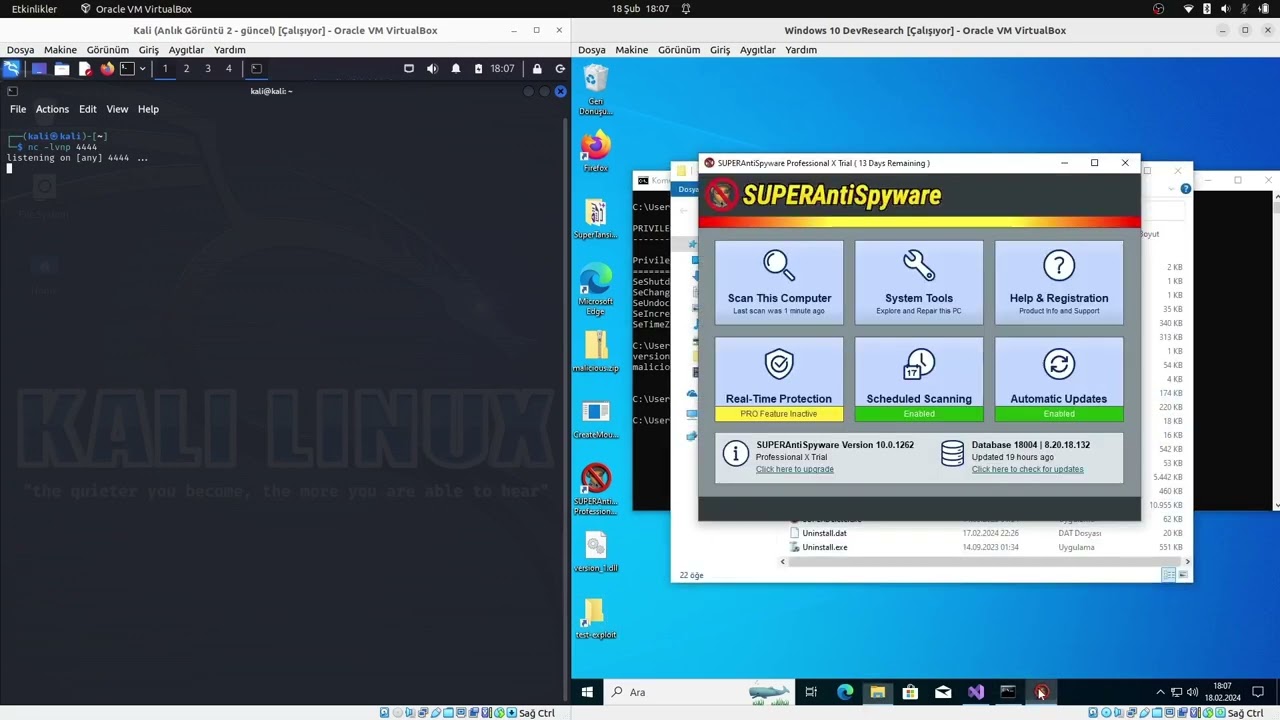
SUPERAntiSpyware Professional X 10.0.1262 is vulnerable to local privilege escalation because it allows unprivileged users to restore a malicious DLL from quarantine into the "C:\Program Files\SUPERAntiSpyware" folder via an NTFS directory junction, as demonstrated by a crafted version.dll file that is detected as malware. Since SASCore64.exe has a DLL Hijacking vulnerability for "version.dll", a shell is obtained as NT AUTHORITY\SYSTEM after system reboot.
Technical details and step by step Proof of Concept's (PoC):
- 1 - A malicious
version.dllfile containing shellcode is created. - 2 - If the generated shellcode containing
version.dllis not already detected by SUPERAntiSpyware, it is combined with another malicious file in ".zip" with the commandcopy /b version_created.dll + malicious.zip version.dllto be detected as malicious. In this way, the created ".dll" file can be detected as malicious by SUPERAntiSpyware and quarantined. - 3 - Create a new folder and copy the prepared
version.dllinto it. Then the folder is scanned and SUPERAntiSpyware quarantines the DLL. - 4 - Using
CreateMountPoint.exeamong the "Symbolic Link Testing" tools provided by Google, the path whereversion.dllis quarantined is mounted in theC:\Program Files\SUPERAntiSpywaredirectory. These tools are available at the following link (https://github.com/googleprojectzero/symboliclink-testing-tools) or you can use the mklink command to do the same thing. - 5 - When the quarantined "version.dll" is restored, it will be copied to SUPERAntiSpyware's directory. After the system reboots, SASCore64.exe will execute the shellcode in "version.dll" and open a session with
NT AUTHORITY\SYSTEMprivileges for the attacker.
Unfortunately, it is not available. We recommend uninstalling SUPERAntiSpyware until the vulnerability is fixed.
- 18.02.2024 - Vulnerability reported via email but vendor refused to fix it.
- 03.04.2024 - Full disclosure.