-
Notifications
You must be signed in to change notification settings - Fork 578
[Examples] Deploy Connectivity Resources
This page describes how to deploy Azure landing zones with connectivity resources based on the Traditional Azure networking topology (hub and spoke) created in the current Subscription context, using the default configuration settings.
NOTE: If you need to deploy a network based on Virtual WAN, please see our Deploy Connectivity Resources (Virtual WAN) example.
As connectivity resources can start to significantly increase Azure consumption costs, the module defaults are aimed to help build the basic connectivity configuration whilst minimizing cost. Please refer to the Network topology and connectivity recommendations to better understand which of these settings you should enable in a Production environment.
In this example, we take the default configuration and make the following changes:
- Set
deploy_connectivity_resourcesto enable creation of the default Connectivity resources, including:- Resource Groups to contain all connectivity resources.
- Virtual Network to use as a hub for hybrid-connectivity.
- Azure private DNS zones for private endpoints.
- Set
subscription_id_connectivityto ensure the Subscription is moved to the correct Management Group, and policies are updated with the correct values.
When deploy_connectivity_resources is set to true, the module updates the parameters and enforcement_mode for a number of policy assignments, to enable features relating to the DDoS protection plan and private DNS zones for private endpoints.
IMPORTANT: Ensure the module version is set to the latest, and don't forget to run
terraform initif upgrading to a later version of the module.
To create the Connectivity resources, deploy_connectivity_resources must be set to true, and the subscription_id_connectivity is also required.
Although subscription_id_connectivity is required, the subscription used for creation of resources is determined by the provider configuration.
Please ensure you have a provider configured with access to the same subscription specified by subscription_id_connectivity, and map this to azurerm.connectivity in the module providers object.
TIP: The exact number of resources created depends on the module configuration, but you can expect upwards of 260 resources to be created by the module for this example.
To keep this example simple, the root module for this example is based on a single file:
# We strongly recommend using the required_providers block to set the
# Azure Provider source and version being used.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.107"
}
}
}
provider "azurerm" {
features {}
}
# You can use the azurerm_client_config data resource to dynamically
# extract connection settings from the provider configuration.
data "azurerm_client_config" "core" {}
# Call the caf-enterprise-scale module directly from the Terraform Registry
# pinning to the latest version
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = "<version>" # change this to your desired version, https://www.terraform.io/language/expressions/version-constraints
default_location = "<YOUR_LOCATION>"
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = "myorg"
root_name = "My Organization"
deploy_connectivity_resources = true
subscription_id_connectivity = data.azurerm_client_config.core.subscription_id
}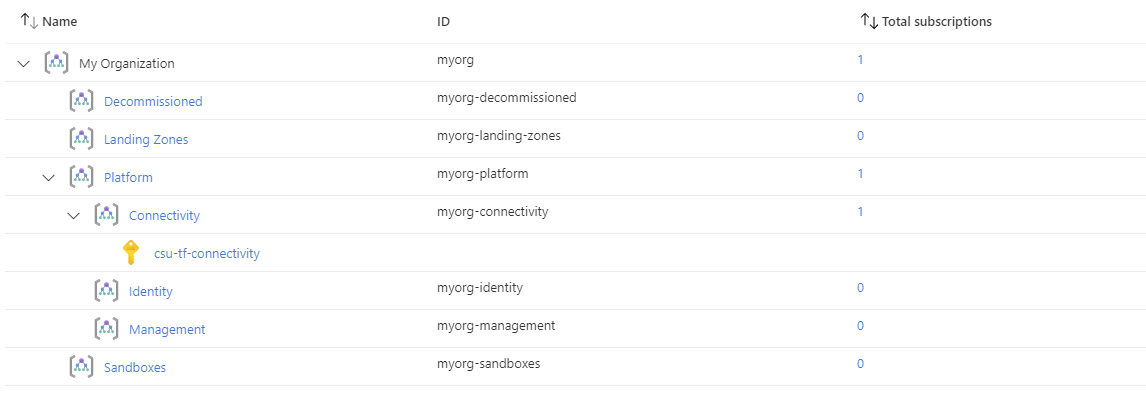
You have successfully created the default management group resource hierarchy, along with the recommended Azure Policy and Access control (IAM) settings for your Azure landing zone.
You have also assigned the current subscription from your provider configuration to the connectivity management group.
Check the following policy assignments to see how these have been configured with default settings for parameters and enforcement mode:
- Scope =
connectivityandlanding-zonesEnable-DDoS-VNET
- Scope =
corpDeploy-Private-DNS-Zones
You may want to Deploy Connectivity Resources With Custom Settings (Hub and Spoke) to change some of these settings.
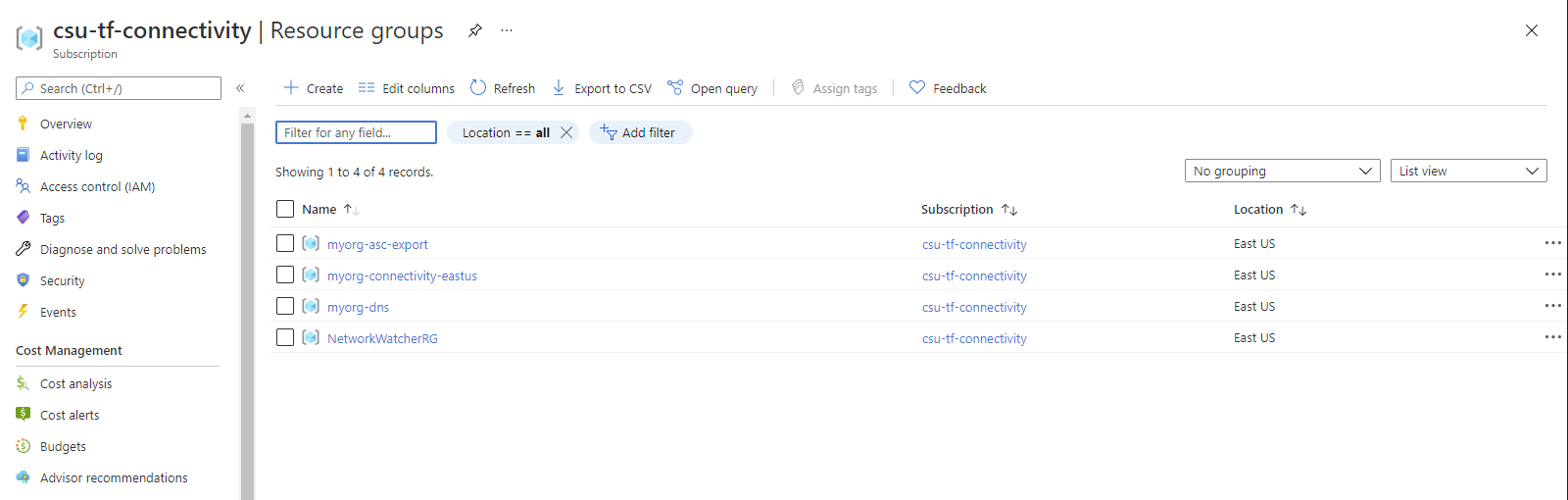
Once deployment is complete and policy has run, you should have the following resource groups deployed in your assigned connectivity subscription:
NOTE:
myorg-asc-exportis related to the management resources. This should contain a hiddenmicrosoft.security/automationsresourceExportToWorkspaceonce the management resources are configured and Azure Policy has completed remediation.NetworkWatcherRGis also automatically generated by the Azure platform when at least one virtual network is created within the subscription.
The Resource Group myorg-connectivity-eastus should be created, and will initially contain a single virtual network with the name myorg-hub-eastus.
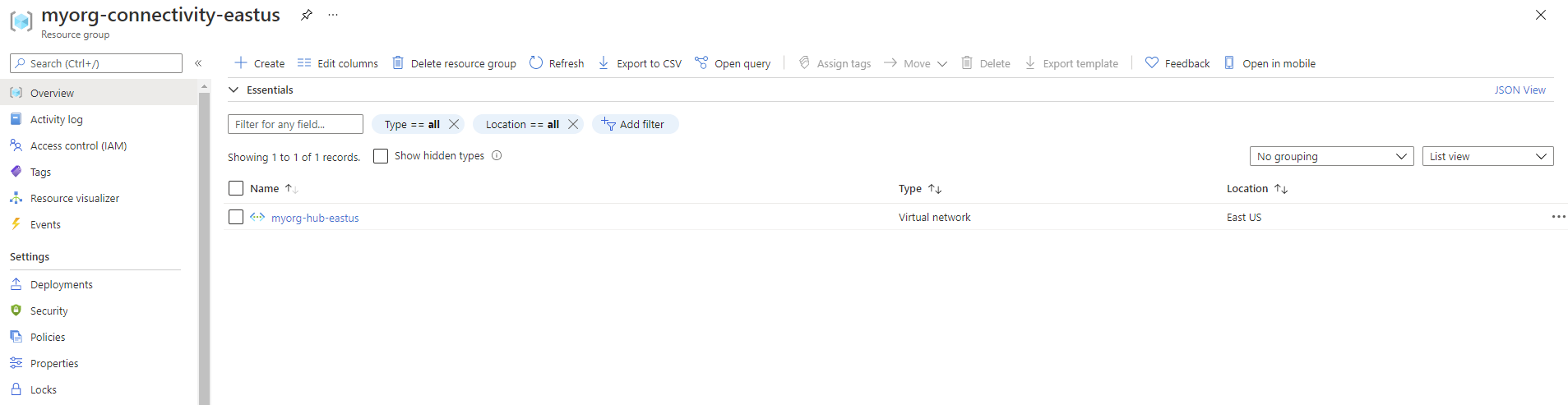
When you explore the configuration, note that myorg-hub-eastus is pre-configured with subnets for GatewaySubnet and AzureFirewallSubnet.
DDoS Network Protection should also be disabled to reduce costs, although we recommend you enable this for production environments.
The location of both the resource group and virtual network is created in the region specified via the default_location input variable, which uses the default value of eastus in this example.
These settings can all be changed if needed!
As DNS resource are Global resources, the resource group is created in the region specified via the default_location input variable, which uses the default value of eastus in this example.
All private DNS zone resources are Global.
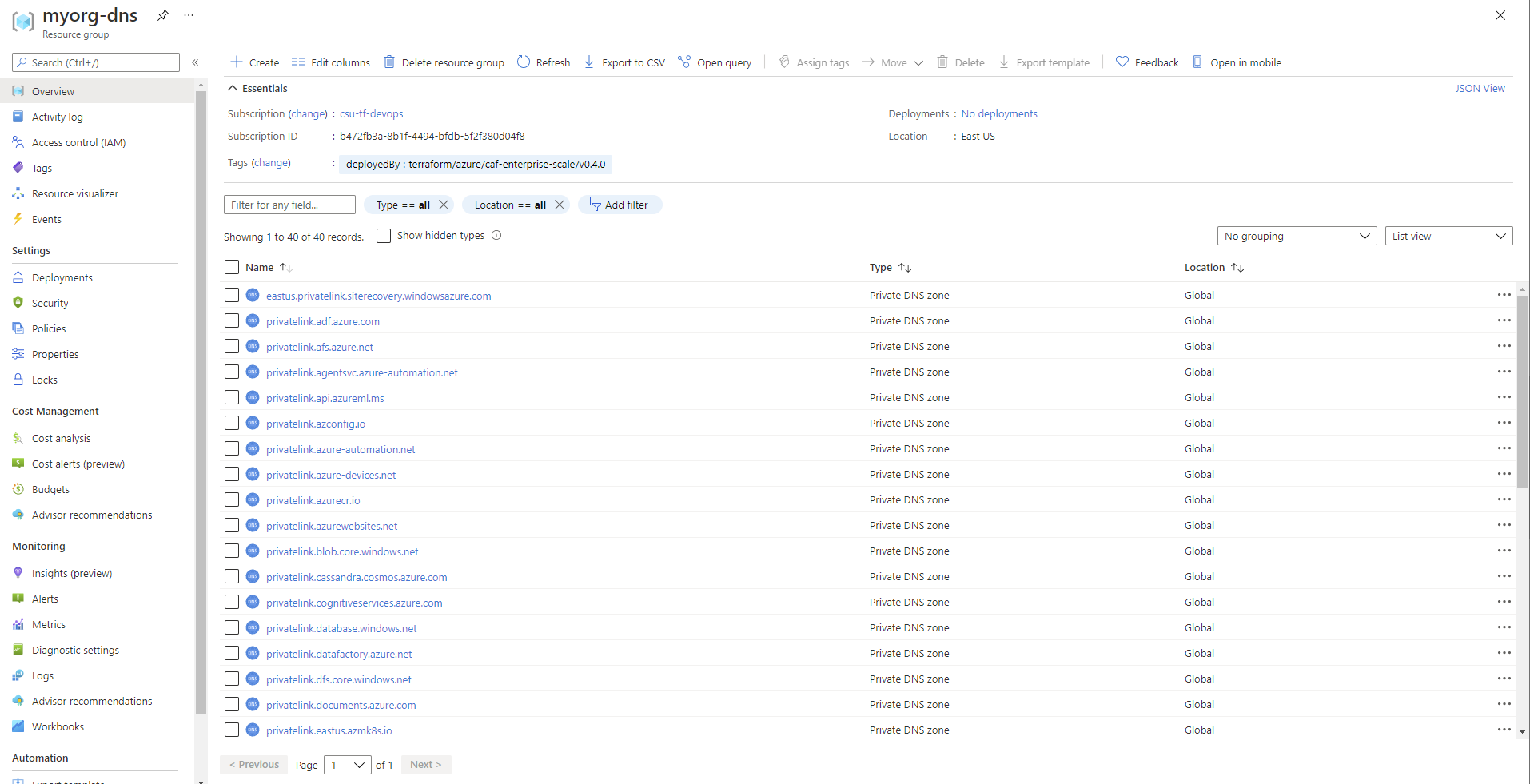
By default we create a private DNS zone for all services which currently support private endpoints. New private DNS zones may be added in future releases as additional services release private endpoint support.
We also configure virtual network links to connect each private DNS zone to the hub virtual network, which in this example is myorg-hub-eastus.
This can be optionally enabled for spoke virtual networks being peered to the hub virtual network.
If you are using archetype exclusions or custom archetypes in your code, make sure to not disable DDoS or DNS policies if you require policy integration using this module. The relationship between the resources deployed and the policy parameters are dependent on specific policy assignments being used.
Go to our next example to learn how to deploy the Connectivity resources with custom settings.
To learn more about module configuration using input variables, please refer to the Module Variables documentation.
Looking for further inspiration? Why not try some of our other examples?
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.
- Home
- User guide
- Video guides
-
Examples
- Level 100
- Level 200
-
Level 300
- Deploy multi region networking with custom settings (Hub and Spoke)
- Deploy multi region networking with custom settings (Virtual WAN)
- Deploy with Zero Trust network principles (Hub and Spoke)
- Deploy identity resources with custom settings
- Deploy management resources with custom settings
- Expand built-in archetype definitions
- Create custom policies, initiatives and assignments
- Override module role assignments
- Control policy enforcement mode
- Policy assignments with user assigned managed identities
- Level 400
- Frequently Asked Questions
- Troubleshooting
- Contributing
