Secure Remote Access Management (WireGuard 2FA/MFA), Identity and Access Management (OpenID Connect SSO), Account Lifecycle (Onboarding)

Website | Getting Started | Features | Roadmap | Support ❤
- WireGuard® VPN with 2FA/MFA - not 2FA to "access application" like most solutions
- The only solution with automatic and real-time synchronization for users' desktop client settings (including all VPNs/locations).
- Control users ability to manage devices and VPN options
- Integrated SSO based on OpenID Connect:
- significant cost saving, simplifying deployment and maintenance
- enabling features unavailable to VPN platforms relying upon 3rd party SSO integration
- Already using Google/Microsoft or other OpenID Provider? - external OpenID provider support
- Only solution with secure remote user Enrollment & Onboarding
- Yubico YubiKey Hardware security key management and provisioning
- Secure and robust architecture, featuring components and micro-services seamlessly deployable in diverse network setups (eg. utilizing network segments like Demilitarized Zones, Intranet with no external access, etc), ensuring a secure environment.
- Enterprise ready (multiple Locations/Gateways/Kubernetes deployment, etc..)
- Built on WireGuard® protocol which is faster than IPSec, and significantly faster than OpenVPN
- Built with Rust for speed and security
See:
Bear in in mind we are no youtubers - just engineers - here is a video introduction to defguard:
Better quality video can be viewed here
- 2FA / Multi-Factor Authentication with TOTP or email based tokens & WireGuard PSK
- automatic and real-time synchronization for users' desktop client settings (including all VPNs/locations).
- Control users ability to manage devices and VPN options
- Defguard instances as well as any WireGuard tunnel - just import your tunnels - one client for all WireGuard connections
- Secure and remote user enrollment - setting up password, automatically configuring the client for all VPN Locations/Networks
- Onboarding - displaying custom onboarding messages, with templates, links ...
- Ability to route predefined VPN traffic or all traffic (server needs to have NAT configured - in gateway example)
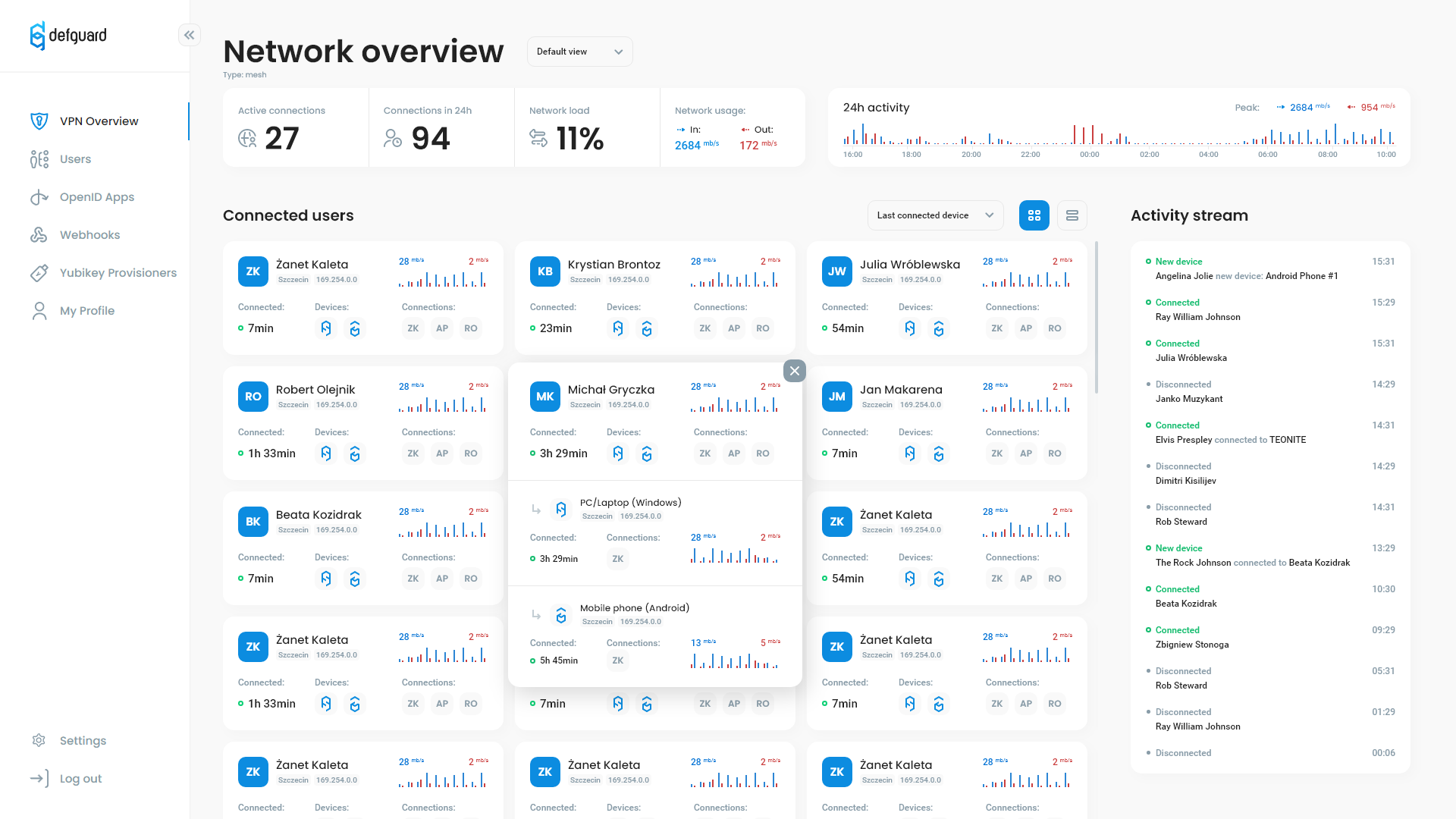
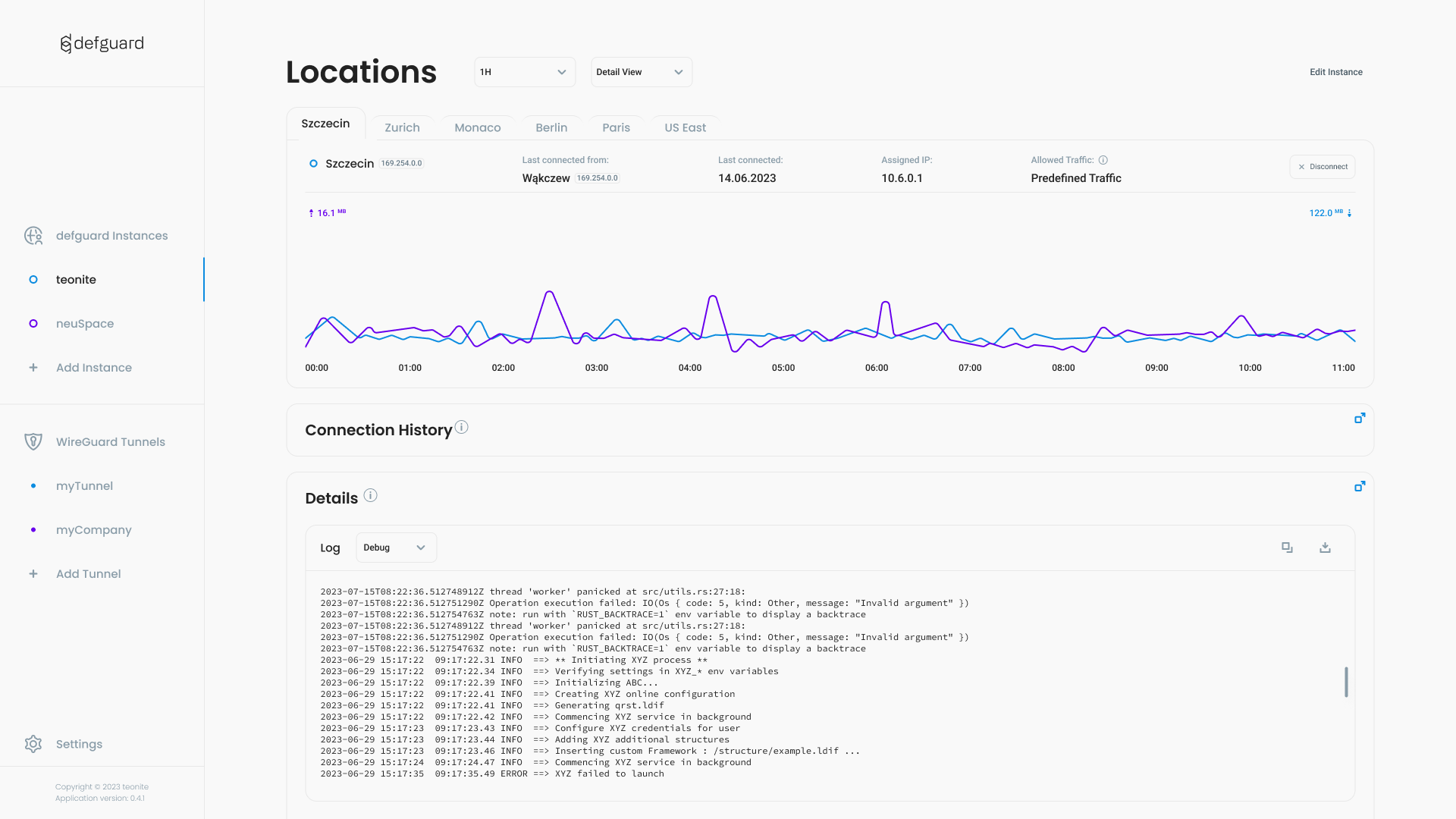
- Live & real-time network charts
- live VPN logs
- light/dark theme
The easiest way to run your own defguard instance is to use Docker and our one-line install script. Just run the command below in your shell and follow the prompts:
curl --proto '=https' --tlsv1.2 -sSf -L https://raw.githubusercontent.com/DefGuard/deployment/main/docker-compose/setup.sh -O && bash setup.shHere is a step-by-step video about this process:
To learn more about the script and available options please see the documentation.
Just follow this tutorial
A detailed product roadmap and development status can be found here
Here is a dedicated view for good first bugs
The story and motivation behind defguard can be found here: https://teonite.com/blog/defguard/
- Remote Access: WireGuard® VPN server with:
- Multi-Factor Authentication with TOTP/Email & Pre-Shared Session Keys
- multiple VPN Locations (networks/sites) - with defined access (all users or only Admin group)
- multiple Gateways for each VPN Location (high availability/failover) - supported on a cluster of routers/firewalls for Linux, FreeBSD/PFSense/OPNSense
- import your current WireGuard® server configuration (with a wizard!)
- most beautiful Desktop Client! (in our opinion ;-))
- automatic IP allocation
- automatic and real-time synchronization for users' desktop client settings (including all VPNs/locations).
- control users ability to manage devices and VPN options
- kernel (Linux, FreeBSD/OPNSense/PFSense) & userspace WireGuard® support with our Rust library
- dashboard and statistics overview of connected users/devices for admins
- defguard is not an official WireGuard® project, and WireGuard is a registered trademark of Jason A. Donenfeld.
- Identity & Account Management:
- SSO based on OpenID Connect](https://openid.net/developers/how-connect-works/)
- External SSO: external OpenID provider support
- Multi-Factor/2FA Authentication:
- Time-based One-Time Password Algorithm (TOTP - e.g. Google Authenticator)
- WebAuthn / FIDO2 - for hardware key authentication support (eg. YubiKey, FaceID, TouchID, ...)
- Email based TOTP
- LDAP (tested on OpenLDAP) synchronization
- forward auth for reverse proxies (tested with Traefik and Caddy)
- nice UI to manage users
- Users self-service (besides typical data management, users can revoke access to granted apps, MFA, WireGuard®, etc.)
- Account Lifecycle Management:
- Secure remote (over the Internet) user enrollment - on public web / Desktop Client
- User onboarding after enrollment
- SSH & GPG public key management in user profile - with SSH keys authentication for servers
- Yubikey hardware keys provisioning for users by one click
- Email/SMTP support for notifications, remote enrollment and onboarding
- Easy support with sending debug/support information
- Webhooks & REST API
- Built with Rust for portability, security, and speed
- UI Library - our beautiful React/TypeScript UI is a collection of React components:
- a set of custom and beautiful components for the layout
- Responsive Web Design (supporting mobile phones, tablets, etc..)
- iOS Web App
- Checked by professional security researchers (see comprehensive security report)
- End2End tests
See the documentation for more information.
Find us on Matrix: #defguard:teonite.com
The code in this repository is available under a dual licensing model:
- Open Source License: The code, except for the contents of the "src/enterprise" directory, is licensed under the AGPL license (see file LICENSE.md in this repository). This applies to the open core components of the software.
- Enterprise License: All code in this repository (including within the "src/enterprise" directory) is licensed under a separate Enterprise License (see file src/enterprise/LICENSE.md).
Please review the Contributing guide for information on how to get started contributing to the project. You might also find our environment setup guide handy.
WireGuard® is registered trademarks of Jason A. Donenfeld.