4Geeks Academy is a start-up focused on software development education. It has a portfolio of over 7,000 active students globally, 5,000 alumni, and a current portfolio of 400 partner companies that hire graduates from their programs. Alejandro Sánchez, CTO of 4Geeks Academy, has contacted you for advice regarding the security of their users and to prevent data breaches.
Develop the following points:
- What should 4Geeks Academy do to prevent their users' data exposure?
- What is the worst that could happen, and why is it so important to maintain data privacy?
- Who should manage the data of students, alumni, and partners?
- What security treatment should the data receive?
- Develop a data recovery plan and a plan to prevent data breaches and protect 4Geeks Academy.
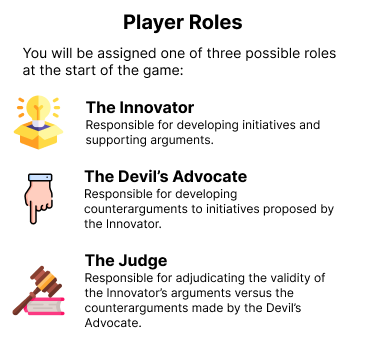
We recommend using this matrix template for following the game, create 2 groups of students: One will represent 👷🏽 the innovator and the other one the 👹 devils advocate. The teacher will be the judge.
Choose to be in one of the groups: 👷🏽 innovator or 👹 devil's advocate and wait for your turn.
Players need no advance preparation. The game requires only that you bring your knowledge, experience, and perspectives to think strategically about critical infrastructure resilience and preparedness.
Before the game, consider a few potential initiatives, such as policies, programs, investments, trainings, partnerships, research and development, or other actions addressing resilience and security implications (threats and opportunities). Consider what initiatives, if successfully implemented today, will help prepare critical infrastructure stakeholders for future challenges.
The game consists of three rounds; during each round, the innovators will propose solutions to security breaches, vulnerabilities, and problems.
- The Innovator first proposes initiatives that could influence critical infrastructure security and resilience in response to a specified disruptive scenario.
- The Devil’s Advocate then provides counterarguments as to why these initiatives may fail, followed by the Innovator’s rebuttal.
- The Judge considers the arguments from both players and assigns each initiative a high, medium, or low probability of success. The assigned probability affects the die roll number needed for the initiative to pass.
Between the Innovator and the Devil’s Advocate, the player who passes (or prevents) the most initiatives is the round’s “winner.” As a reward.
Proposal 1: Implementation of Multi-Factor Authentication (MFA)
Details: The Innovator proposes implementing multi-factor authentication (MFA) for all user, employee, and partner accounts at 4Geeks Academy. This measure will significantly enhance security by requiring a second form of verification in addition to the password.
Benefits:
- Increased Security: MFA makes it more difficult for attackers to access accounts, even if they obtain passwords.
- Protection Against Phishing: Adds an additional layer of defense against phishing attacks.
- Regulatory Compliance: Helps comply with security and data protection regulations.
Counterargument: The Devil's Advocate points out that implementing MFA may face several challenges and may not be sufficient on its own to ensure complete security.
Challenges:
- User Resistance: Users may find MFA inconvenient and resist its implementation, which could affect user experience and adoption.
- Additional Costs: Implementing and maintaining MFA can involve significant additional costs in terms of technology and customer support.
- Not a Complete Solution: While MFA increases security, it does not address other potential vulnerabilities such as outdated software, incorrect system configurations, and lack of cybersecurity education.
Response Proposed by The 👷🏽 Innovator:
Response: The Innovator can respond by acknowledging the challenges mentioned and proposing additional solutions to address them:
- Education and Communication: Launch an educational campaign to explain the benefits of MFA to users and employees, reducing resistance and increasing adoption.
- Gradual Implementation: Introduce MFA gradually, starting with employees and the most sensitive users, and then extending it to all users.
- Complementary Security Measures: Ensure that MFA is part of a comprehensive security approach that includes regular software updates, security audits, and ongoing cybersecurity training.