In AuctionDemo, a user can win the auctionned token and get his funds back
#1252
Labels
3 (High Risk)
Assets can be stolen/lost/compromised directly
bug
Something isn't working
duplicate-1323
satisfactory
satisfies C4 submission criteria; eligible for awards
Lines of code
https://github.com/code-423n4/2023-10-nextgen/blob/8b518196629faa37eae39736837b24926fd3c07c/smart-contracts/AuctionDemo.sol#L104-L120
https://github.com/code-423n4/2023-10-nextgen/blob/8b518196629faa37eae39736837b24926fd3c07c/smart-contracts/AuctionDemo.sol#L104-L105
https://github.com/code-423n4/2023-10-nextgen/blob/8b518196629faa37eae39736837b24926fd3c07c/smart-contracts/AuctionDemo.sol#L124-L125
Vulnerability details
Impact
Because of combination of multiples issues in the
AuctionDemocontract, a malicious user can make a sandwich attack on another user to take the auctionned token/NFT and recover his funds.Proof of Concept
In the
AuctionDemocontract, we have multiples problems.Firstly, I think for a more safe auction process, when an auction is ended, we mustn't be able to re-bid.
And we can see the functions
participateToAuction(),cancelBid()andcancelAllBids()makes a require check for time thatblock.timestamp <= auctionEndTime:And function
claimAuction()make a require check for time thatblock.timestamp >= auctionEndTime.As the result when
block.timestamp == auctionEndTime, users can potentially claim, participate to the auction and cancel a bid.There's also the following problem. The status of an auctionInfoData (
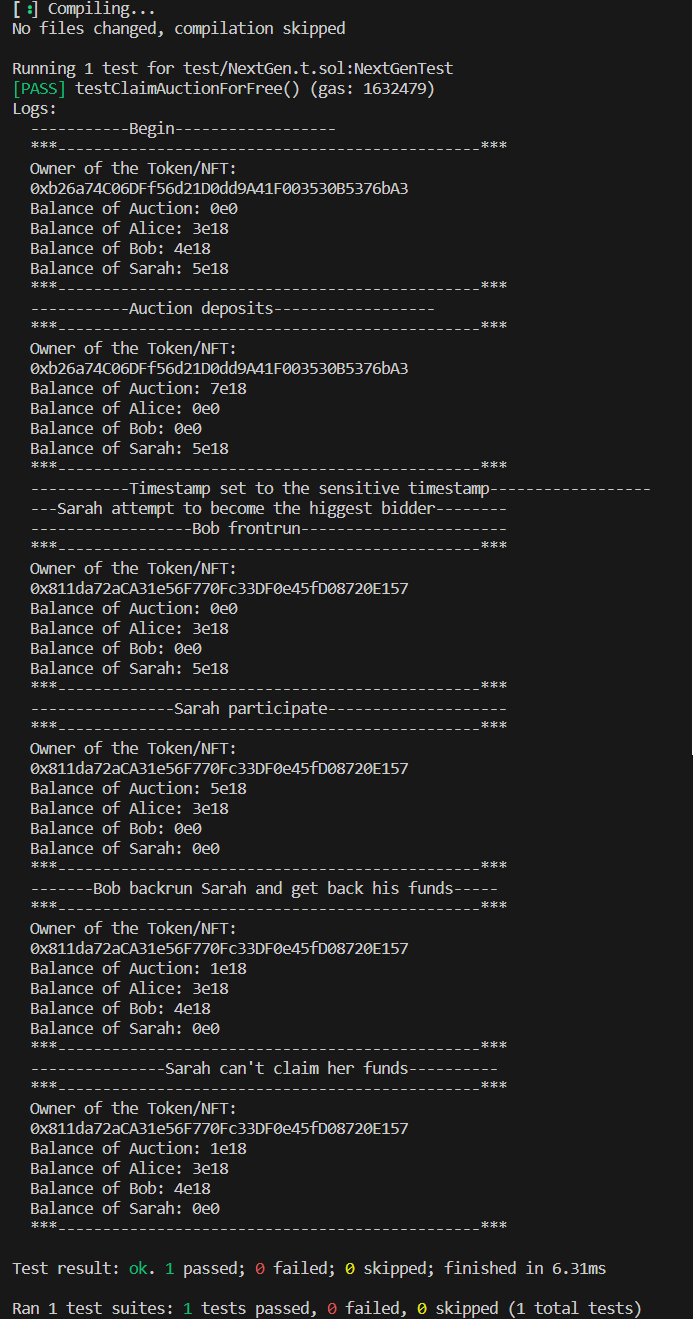
auctionInfoData[_tokenid][index].status) is set to true insideparticipateToAuction()and set to false incancelBid()andcancelAllBids(). This permit to verify if for an index of the array, the bid is claimable or not. The problem inside theclaimAuction()is the status is not set to false when ETH are send to the user, this problem turn to a vulnerability in the scenario below.Because of the time checking problem in the contract functions, check this potential scenario of a sandwich attack:
participateToAuction()block.timestampclaimAuction(). Bob claim the tokens because it's the highest bidder and all the bids are send back to all bidders.cancelBid()for his bid. Because the contract doesn't set theauctionInfoData[_tokenid][index].statusto false inclaimAuction()and now the contract have the Sarah funds (which is of course more than the Bob amount because Sarah send a transaction to be the highest bidder), Bob retrieve his funds by stealing Alice's deposit.Bob won the Token/NFT for free and he steal the funds of a user.
Now Alice can't withdraw her deposited ETH because the
AuctionDemobalance is less than her bid and all call toclaimAuction()orcancelBid()wil revert.And if the same contract is used to auction other tokenId, Alice can withdraw her ETH but impossibility to use
claimAuction()for other tokenId because there are an offset between the internal balance of the contract and values saved in all theauctionInfoData[_tokenid][i].bid.Logs
You have the image with the logs of the PoC
You can check this Gist to setup foundry with the smart contracts for an executable PoC:
https://gist.github.com/AxelAramburu/c10597b5ff60616b8a15d091f88de8da
And execute this command:
forge test --mt testClaimAuctionForFree -vvvTools Used
Manuall Review, Foundry
Recommended Mitigation Steps
You can fix this issue by change the time check in the
claimAuction()function, you have also to set theauctionInfoData[_tokenid][i].statusto false when the ETH are redeemed:Assessed type
Timing
The text was updated successfully, but these errors were encountered: