A reverse engineering tool to restore stripped symbol table for iOS app.
Example: restore symbol for Alipay

-
- Download source code and compile.
git clone --recursive https://github.com/tobefuturer/restore-symbol.git
cd restore-symbol && make
./restore-symbol
-
- Restore symbol using this command. It will output a new mach-o file with symbol.
./restore-symbol /pathto/origin_mach_o_file -o /pathto/mach_o_with_symbol
-
- Copy the new mach-o file (with symbol) to app bundle, replace the origin mach-o file with new mach-o file. Resign app bundle.
codesign -f -s "iPhone Developer: XXXXXXX" --signing-time none --entitlement ./xxxx.app.xcent ./xxxx.app
-
- Install the app bundle to iOS device, and use lldb to debug the app. Maybe you can use the
ios-deploy, or other way you like. If you useios-deploy, you can execute this command.
- Install the app bundle to iOS device, and use lldb to debug the app. Maybe you can use the
brew install ios-deploy
ios-deploy -d -b xxxx.app
-
- Now you can use
b -[class method]to set breakpoint.
- Now you can use
-
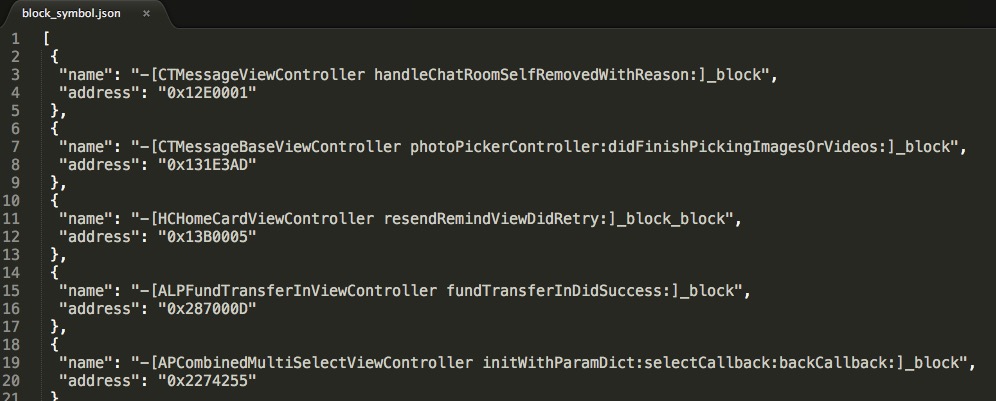
- Search block symbol in IDA to get json symbol file, using script(
search_oc_block/ida_search_block.py) .
- Search block symbol in IDA to get json symbol file, using script(
-
- Use command line tool(restore-symbol) to inject oc method symbols and block symbols into mach o file.
./restore-symbol /pathto/origin_mach_o_file -o /pathto/mach_o_with_symbol -j /pathto/block_symbol.json
-
- Other steps(resign, install, debug) are samen as above.
Usage: restore-symbol -o <output-file> [-j <json-symbol-file>] <mach-o-file>
where options are:
-o <output-file> New mach-o-file path
--disable-oc-detect Disable auto detect and add oc method into symbol table,
only add symbol in json file
--replace-restrict New mach-o-file will replace the LC_SEGMENT(__RESTRICT,__restrict)
with LC_SEGMENT(__restrict,__restrict) to close dylib inject protection
-j <json-symbol-file> Json file containing extra symbol info, the key is "name","address"
like this:
[
{
"name": "main",
"address": "0xXXXXXX"
},
{
"name": "-[XXXX XXXXX]",
"address": "0xXXXXXX"
},
....
]