-
Notifications
You must be signed in to change notification settings - Fork 35
Options
A description of the available DKIM Verifier options. A description of the account specific Options can be found here.
If enabled the add-on verifies the DKIM signatures. This option does not affect the reading of the Authentication-Results header.
In the account specific options, this behavior can be changed for each account.
Option available since version 1.5.0.
Set whether DKIM keys should be cached. Available options:
Don't store DKIM keysStore DKIM keysStore DKIM keys and compare them with the current key
If storing is enabled the stored keys can be viewed by pressing the DKIM keys button. There keys can also be deleted or changed. To update the used DKIM key of the currently viewed e-mail select Update DKIM key in the DKIM drop-down menu in the e-mail header (although this should almost never be necessary).
Versions before 4.x stored the keys in the dkimKey.sqlite SQLite database in the profile directory.
If enabled the results of the verification is saved.
The saved result of the currently viewed e-mail can be updated by selecting Reverify DKIM signature in the DKIM drop-down menu in the e-mail header.
If enabled the add-on first tries to read the DKIM, SPF and DMARC results from the Authentication-Results header instead of verifying the DKIM signature.
In the account specific options, this behavior can be changed for each account. It is also possible to only trust specific servers.
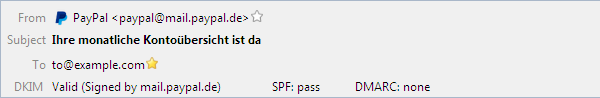
Option available since version 1.3.0 (prior to 1.4.0 in Advanced).
DNS specific options. More Information can be found in DNS Options.
Enable this if the add-on should try to determine based on sign rules whether an e-mail should be signed.
If enabled the default sign rules are used in addition to the ones created by the user.
If this is enabled the add-on adds a sign rule for every viewed e-mail with a valid DKIM signature for which no sign rule yet exist.
If this is enabled sign rules are only automatically added if the From address is in the SDID.
Option available since version 1.1.0.
Slecte which addresses the automatically added sign rule should affect.
Available options (example for an e-mail from from@subdomain.example.com):
-
for From addresseffects only e-mails from from@subdomain.example.com -
for subdomaineffects all e-mails from subdomain.example.com -
for base domaineffects all e-mails from example.com
Option available since version 1.1.0.
If enabled, the SDID in the DKIM signature must not be exactly the same as the one specified in the sign rule, but can also be a subdomain.
Option available since version 1.2.0.
Normally a SDID different from the one specified in the matched sign rule results in an invalid DKIM signature. Enable this it should be treated as a warning instead.
If this is enabled and no matching sign rule was found for an e-mail, the add-on tries to determine if the e-mail should be signed based on DMARC. As this uses DMARC in a non standard conform way the result may not always be right.
It works in the following way:
If a valid DMARC entry is found for the domain or base domain of the From address of the e-mail the e-mail is marked as should be signed. extensions.dkim_verifier.policy.DMARC.shouldBeSigned.neededPolicy can be set to none, quarantine or reject. If set to quarantine the e-mail is only marked as should be signed if the domain specifies in DMARC that invalid e-mails should be flaged as suspicious or be rejected, with reject only if they should be rejected. With the default none the e-mail is always marked as should be signed if a DMARC entry was found.
Option available since version 1.1.0.
By pressing the Signers rules or Default signers rules button the user specific and the default sign rules can be viewed. At the Signers rules button the user specific sign rules can also be added, modified or deleted.
This options warns about headers that are unsigned but are either shown directly, affect how the body of the e-mail is shown or affect how Thunderbird behaves.
-
relaxed mode: Will try to avoid showing warnings and only require the most important headers to be signed. -
recommended mode: Enforce signing of relevant headers without showing to many warnings. -
strict mode: Enforce signing of all relevant headers.
Note that besides the From header the DKIM standard itself does not require any other header to be signed.
Option available since version 5.1.0.
With this options it can be specified how the result for the DKIM signature should be shown. More Information can be found in Display Options.
If enabled not only errors but debugging information too is shown in the Error Console. Details about the available debug options can be found here.
Show more detailed error reasons for why a signature verification failed. This can be very technical, so a deeper knowledge of the DKIM standard is required to understand them.
Option available since version 1.4.0.
Normally an e-mail signed by a domain which is only testing DKIM is treated as not being signed. Only if this is enabled will the DKIM signature be verified and the result shown. A warning will be added if the domain is testing DKIM.
If the DKIM key was successfully validated by DNSSEC, a Lock is shown after the SDID. This only works if the selected DNS resolver supports DNSSEC.
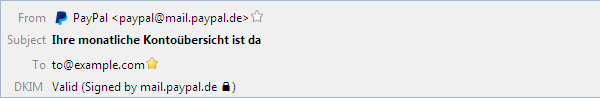
Option available since version 1.6.0.
If disabled, the result of the Authentication-Results header is shown in addition to the DKIM verification result of the add-on. Note that the reading of the Authentication-Results must be enabled separately.
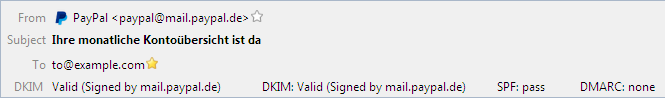
Option available since version 1.6.0.
If enabled, the following violations of the RFC 7601 are ignored while parsing the Authentication-Results header:
- trailing
;at the end of the header -
/in theheader.b(or another) property, even if it is not in a quoted-string -
:in theheader.b(or another) property, even if it is not in a quoted-string (since version 5.4.0)
Option available since version 2.0.0.
Specify how an ill-formed AUID tag should be treated. According to the RFC 6376 this is an error. The default is warning because this is only a violation with small effect and some legitimate DKIM signature are violating this.
Specify how an ill-formed but still usable selector tag should be treated. According to the RFC 6376 this is an error. The default is warning because this is only a violation with small effect and some legitimate DKIM signature are violating this.
Option available since version 1.3.0.
Specify how an DKIM key not not signed by DNSSEC should be treated. This only works if the selected DNS resolver supports DNSSEC.
If the DKIM keys are stored they can be set to secure manually in the options or by selecting Mark DKIM key as secure in the DKIM drop-down menu in the e-mail header.
Specify how the usage of the rsa-sha1 algorithm for signing is treated. As SHA-1 is no longer considered secure, usage of rsa-sha1 in DKIM was forbidden by the RFC 8301.
The default is warning only because rsa-sha1 seems to be still widely used, and not because this is not considered a security risk.
Option available since version 2.1.0.
Specify how the usage of an RSA key with less than 2048 bits for signing is treated. According to RFC 8301, keys should be at least 2048 bits.
Keys with less than 1024 bits will always be treated as an error.
The default is nothing only because 1024 bit keys seems to be still widely used, and not because this key size is still recommended to use.
Option available since version 2.2.0/3.1.0.