A collection of scripts for finding threats in Office365
A tool for finding risky or suspicious inbox rules - more detail in this post
This tool requires Reqeusts, Requests-cache and Jinja2 - these can be installed with pip install -r requirements.txt
It requires an administrative access to AzureAD & Office365 environment to set up but no specific account is required for its continued use.
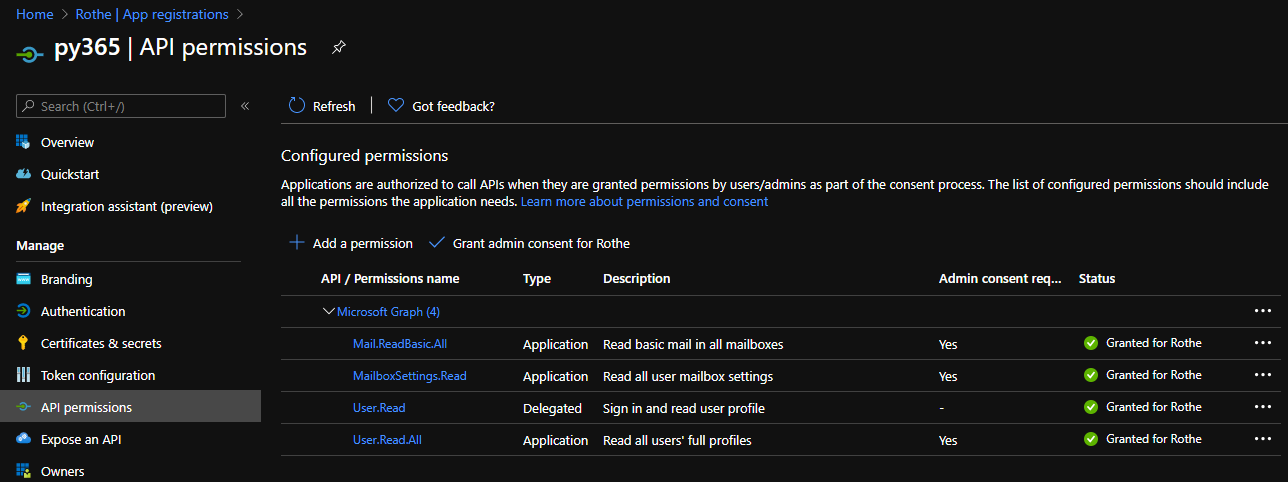
You will need to create a new application registration in the AzureAD portal and grant it the following permissions at the application level and grant admin consent for them:
- Microsoft Graph
- Mail.ReadBasic.All
- MailboxSettings.Read
- User.Read.All
Next, generate a secret and make a record of the secret string as well as the app/client ID. You will then need to make a copy of config.example.py and update it with your own domain, app id and secret
Just run riskyrules.py - no arguments are required and once the script has finished the report will be saved as report.html in the current directory