-
Notifications
You must be signed in to change notification settings - Fork 981
Whats new
-
Updates
- December 2024
- November 2024
- 🔃 Policy Refresh Q1 FY25
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- 🆕 AMA Updates
- 🔃 Policy Refresh H2 FY24
- May 2024
- April 2024
- March 2024
- February 2024
- AMA Update for the Portal Accelerator
- 🔃 Policy Refresh Q2 FY24
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- Previous Updates
Enterprise Scale/Azure Landing Zones is updated regularly. This page is where you'll find out about the latest updates to Enterprise Scale/Azure Landing Zones for:
-
CAF (Cloud Adoption Framework) Documentation Updates
- Check out the CAF specific What's new in the Microsoft Cloud Adoption Framework for Azure page
- Improvements to existing guidance and artifacts
- Azure Policy changes
- Bug fixes
- Updated broken links in Deploying ALZ ZT Network
- Tooling updates:
Note: Please check the latest release notes for each of the tools, as these will contain more detailed notes relating to changes in each of the tools.
This article will be updated as and when changes are made to the above and anything else of relevance for Enterprise Scale/Azure Landing Zones. Make sure to check back here often to keep up with new updates and changes.
Important: Previous changes to the above in relation to Enterprise Scale will not be listed here. However going forward, this page will be updated.
Here's what's changed in Enterprise Scale/Azure Landing Zones:
- Updated the Baseline alerts and monitoring integration section in the portal accelerator to deploy the latest release of AMBA (2024-12-10). To read more on the changes, see the What's new page in the AMBA documentation.
- A bug was resolved in the Portal Accelerator that caused deployment validation to fail with the error message "The 'location' property must be specified for 'amba-id-amba-prod-001'". This event happened when a Log Analytics Workspace was not deployed, but Azure Monitor Baseline Alerts were enabled. This issue occurred because Azure Monitor Baseline Alerts depend on the management subscription, which is not provided if the Log Analytics Workspace is not deployed. To address this scenario, an additional section was implemented in the Baseline alerts and monitoring tab allowing the selection of a Management subscription when not deploying a Log Analytics Workspace.
- Updated the Baseline alerts and monitoring integration section in the portal accelerator to deploy the latest release of AMBA (2024-11-01). To read more on the changes, see the What's new page in the AMBA documentation.
- Link for the Bicep Subscription Vending changed to AVM (Azure Verified Modules)
- Updated ALZ custom policies enforcing minimum TLS versions to properly evaluate the minimum TLS version, ensuring services configured to deploy TLS 1.3 will successfully evaluate.
- Updated the initiative Deploy-MDFC-Config_20240319 to the the newer version of DCSPM: Configure Microsoft Defender CSPM plan
- Updated Deploy-Private-DNS-Generic policy to include the ability to configure the location/region.
- Removed duplicate assignment and portal option of Deploy Azure Policy Add-on to Azure Kubernetes Service clusters at Landing Zones scope, as this policy is assigned in the initiative Deploy Microsoft Defender for Cloud configuration at Intermediate Root scope.
- Updated the Deny-vNet-Peer-Cross-Sub.json definition policy to include a parameter for allowed virtual networks (vNets) in other subscriptions. For vNets to be permitted to peer, both vNet IDs must be added to the allowed list.
- Added new built-in policy assignment and portal option for Subnets should be private assigned at Platform and Landing Zones management groups. This policy's assignment effect is defaulted to "Audit" in this release, giving the community time to adopt the good practice and address subnet compliance. We will default to the "Deny" effect as part of the next Policy Refresh.
- Added option to select Diagnostic Settings category for logging to Log Analytics in the portal experience. You can now select between the recommended "All Logs" which covers almost all Azure resources, or "Audit Only" which is limited to resources that support this category.
- Added additional built-in policies to initiatives for the following Azure AI Services:
- Azure OpenAI
- Cognitive Services/Search -> AI Services
- Machine Learning
- Bot Service (new) -> AI Bot Services
- Updated the initiative Deploy-MDFC-Config_20240319 to include an additional parameter that allows you to specify if the Defender for Cloud export to Log Analytics should create a new resource group. This is useful when you want to specify the resource group name or requires tags on resource groups. Will be used by other RIs - Terraform and Bicep (portal accelerator will use default values).
- Updated Automation Account to disable local authentication by default.
- Updated the initiative Deploy-Private-DNS-Zones to reduce the number of parameters required while retaining backward compatibility. The initiative now only requires the subscription ID, resource group name, and location for the private DNS zone. The DNS zone resource id is now generated based on those inputs. This simplifies usage in the upstream Terraform and Bicep modules.
Note: there a known issue when re-deploying ALZ using the portal accelerator with CMK enabled. For details please see Known Issues.
- Resolved a bug in the Portal Accelerator related to deploying the single platform subscription setup. Incorrect parameter settings led to the failure of AMBA, as it erroneously attempted to deploy to a standard management group structure instead of a single platform management group as needed.
- Increasing Policy assignment delay by a couple of minutes to help reduce assignment errors using the portal accelerator experience (the infamous "please wait 30 minutes and try again" error).
- An issue with the Portal Accelerator regarding the Azure Monitor Baseline Alerts notifications settings was resolved. The problem occurred when no Email Address or Service Hook was specified on the Baseline alerts and monitoring tab. In this scenario, an empty string was converted to an array, resulting in the format
[""]instead of[]. This caused errors during the remediation of the Notification Assets initiative.
- The ALZ Policies and ALZ Deprecated Services documentation has been updated to reflect changes in AMBA. To provide more flexibility for future growth AMBA is transitioning from a single Landing Zone policy initiative and instead is adopting a modular approach by splitting the Landing Zone initiative into the following distinct components (initiatives):
- Key Management
- Load Balancing
- Network Changes
- Recovery Services
- Storage
- VM
- Web
- Guidance for updating and implementing these changes in existing environments is available on the AMBA website.
- Updated the Azure Monitoring Baseline Alerts (AMBA) integration section in the portal accelerator to include new features exposed by the AMBA solution. To read more on the changes https://azure.github.io/azure-monitor-baseline-alerts/patterns/alz/Whats-New/
- The September community call recording and slides have been uploaded to YouTube and wiki, all available from aka.ms/alz/community
NOTE TO CONTRIBUTORS: Due to security compliance requirements, we've made core changes that mean we no longer automatically build the policies, initiatives and roles templates after changes in the
srcfolder are committed. This means that you as a contributor must run the bicep build commands to generate the required outputs as part of your pull request. Depending on the files you've updated these are the commands (assuming you have bicep installed):
bicep build ./src/templates/policies.bicep --outfile ./eslzArm/managementGroupTemplates/policyDefinitions/policies.jsonbicep build ./src/templates/initiatives.bicep --outfile ./eslzArm/managementGroupTemplates/policyDefinitions/initiatives.jsonbicep build ./src/templates/roles.bicep --outfile ./eslzArm/managementGroupTemplates/roleDefinitions/customRoleDefinitions.json
- Cleaned up the Log Analytics "solutions" in portal ARM template, as these are no longer required and deployed by ALZ.
- Re-introduced the option to enable "Sentinel" in the portal accelerator.
- Updated Microsoft Sentinel onboarding (enablement) using the new mechanism that fixes issues after 1 July 2024. Microsoft Sentinel is enabled by default through the portal accelerator as a best practice - we do not however configure any data connectors, we only enable the service. Should you wish to remove this, you can delete the association from the Azure Portal after deployment from the "Sentinel" feature blade.
- Fixed a bug that would result in a failed deployment if deploying an Express Route Gateway and Basic Firewall SKU through the portal accelerator.
- Fixed a bug that would result in a failed deployment for some multi-region Virtual WAN scenarios with identity networks and gateways.
- Fixed a bug that had ALZ-LITE deployments try to connect DNS zones twice for single regions deployment.
- Alignment of allowedValues in the following initiatives with those used in the included policyDefinitions:
- As the Log Analytics agent is set to be retired on August 31, 2024, it is crucial for users to plan their migration to avoid any disruption in their monitoring services. The migration involves understanding the current setup, including agents, workspaces, solutions, insights, and data collections, and then configuring the new data collections to ensure a smooth transition. Tools like the AMA Migration Helper and DCR Config Generator can assist in automating and tracking the migration process. We've now made available migration guidance to assist in the process.
- Developed a script to facilitate the transition from Microsoft Monitoring Agent (MMA) to Azure Monitor Agent (AMA) within Azure landing zones. Review the migration guidance for additional information on how the script can be used.
- General update AMA documentation ALZ AMA Update
- Added new custom policy Do not allow deletion of specified resource and resource type that provides a safeguard against accidental removal of the User Assigned Managed Identity used by AMA. Assigned at the Platform Management Group, it blocks delete calls using the deny action effect.
- Updated the custom policy Deploy-ASC-SecurityContacts as part of the Deploy-MDFC-Config initiative to use the new API and revised construct for the Security Contact API in Defender for Cloud (
alertNoticationsalias has been deprecated, and replaced bynotificationSources).
- 12th June 2024 ALZ External Community Call recording and slides uploaded and shared here
The ALZ Portal Accelerator has been enhanced with the latest AMA updates, ensuring a seamless and efficient management experience. 🚀
Key updates include:
-
Azure Landing zones is now using a single centralized User Assigned Managed Identity. The centralization of User Assigned Managed Identity for Azure Monitor Agent (AMA) marks a significant advancement in our ability to manage large-scale deployments efficiently.
- The User Assigned Managed Identity
id-ama-prod-<location>-001is created in resource group<enterpriseScaleCompanyPrefix>-mgmtin the management subscription or in the platform subscription when selecting 'Single' in the Platform subscription options. - The feature flag
restrictBringYourOwnUserAssignedIdentityToSubscriptionhas been added to the policies and initiatives that enables the use of a single centralized User Assigned Managed Identity.-
restrictBringYourOwnUserAssignedIdentityToSubscriptionset as True (Policy/Initiative default): Restricts the bring your own UAMI to a UAMI from the same subscription as the VM. -
restrictBringYourOwnUserAssignedIdentityToSubscriptionset as False (ALZ Default): Removes that restriction and allows you to assign your own UAMI from any subscription within the tenant/ scope of assignment.
-
- We've updated the following built-in policy initiatives to support single User Assigned Managed Identities:
- Enable Azure Monitor for VMs with Azure Monitoring Agent(AMA)
- Enable Azure Monitor for VMSS with Azure Monitoring Agent(AMA)
- Configure SQL VMs and Arc-enabled SQL Servers to install Microsoft Defender for SQL and AMA with a user-defined LA workspace
- [Preview]: Enable ChangeTracking and Inventory for virtual machines
- [Preview]: Enable ChangeTracking and Inventory for virtual machine scale sets
- The User Assigned Managed Identity
-
Custom Defender for SQL initiative has been deprecated and is replaced by Configure SQL VMs and Arc-enabled SQL Servers to install Microsoft Defender for SQL and AMA with a user-defined LA workspace
-
Custom User Assigned Managed Identity policy has been deprecated. UAMI for AMA is now centrally deployed therefore this policy is no longer required.
-
When utilizing Portal, ARM, or Bicep, it is necessary to manually remove policy assignments corresponding to deprecated policies. To proceed with the deletion of the assignment, please refer to the Display Name or Assignment Name provided below.
Assignment Name Display Name Scope of Assignment Deploy-MDFC-DefenSQL-AMA Configure SQL VMs and Arc-enabled SQL Servers to install Microsoft Defender for SQL and AMA with a user-defined LA workspace Platform Management Group
Landing Zones Management GroupDeploy-UAMI-VMInsights Deploy User Assigned Managed Identity for VM Insights Landing Zones Management Group
We've missed Q3 timelines completely, but for good reason. We've held back this cycle of Policy Refresh in order to address some key initiatives that we feel are critical to the success of our customers. This is the single largest update to the ALZ Policy since the inception of the project. We're excited to share these updates with you, and we're confident that they will provide significant value to your deployments and the compliance of your Azure Landing Zones.
- 📌Major Update: New "Workload Specific Compliance" section added to ALZ Portal accelerator. This will allow you to apply compliance policies to specific workloads, such as SQL, Storage, and more. These additional compliance controls are frequently required by highly regulated industries like financial services, healthcare, etc. Note: they are not assigned by default, you are required to select the workload and management group scope to apply assignments. For more information review ALZ Policy - Extra
This release includes:
- 25 new custom initiatives added to support key Azure workloads/services
- Significantly enhanced Deny-PublicPaasEndpoints to cover additional services (no public access)
- Significantly enhanced Enforce-EncryptTransit to cover additional services (TLS and SSL)
- Significantly enhanced Enforce-EncryptionCMK to cover additional services (customer managed keys)
- 24 new custom policies added for various workloads where no equivalent built-in policy is available (included in the new initiatives) - please note some policies only support the "Audit" effect, and should be overridden as needed.
- 🎉Diagnostic Settings v2 have arrived covering 140 Azure services and greatly simplifying implementation and management.
- Updated the diagnostic settings assignment to use the new built-in initiative Enable allLogs category group resource logging for supported resources to Log Analytics
- Deprecating the ALZ custom diagnostic settings policies (53) and initiative (1)
- NOTE: going forward if you have issues with Diagnostic Settings, please open an Azure support ticket
- Updated Audit-PublicIpAddresses-UnusedResourcesCostOptimization to check for
staticpublic IP addresses that are not associated with any resources (instead ofnot basic). - Fixed the bug with Configure Azure Machine Learning workspace to use private DNS zones policy where
secondPrivateDnsZoneIdparameter was missing which was leaving AML private endpoints incomplete. - Updated
Audit-PrivateLinkDnsZonesdisplay name to include the fact it can beauditordeny - Added the Configure BotService resources to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Azure Managed Grafana workspaces to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Azure Virtual Desktop hostpool resources to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Azure Virtual Desktop workspace resources to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Azure Device Update for IoT Hub accounts to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Azure Arc Private Link Scopes to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Deploy - Configure IoT Central to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure Recovery Services vaults to use private DNS zones for backup built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure a private DNS Zone ID for table groupID built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Added the Configure a private DNS Zone ID for table_secondary groupID built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
- Removed Defender for Cloud for DNS, as this is now deprecated and is included in Defender for Servers. Deprecated Deploy-MDFC-Config initiative, and superseded with Deploy-MDFC-Config_20240319 to minimize breaking change impact on existing deployments.
- Removed Defender for Cloud for APIs, as this is now deprecated due to plan changes for this service. Deprecated Deploy-MDFC-Config initiative, and superseded with Deploy-MDFC-Config_20240319 to minimize breaking change impact on existing deployments.
- Added new initiative and default assignment for Enforce-Backup scoped to the Landing Zones and Platform management groups in Audit mode:
- Added the [Preview]: Immutability must be enabled for backup vaults built-in policy
- Added the [Preview]: Immutability must be enabled for Recovery Services vaults built-in policy
- Added the [Preview]: Soft delete should be enabled for Backup Vaults built-in policy
- Added the [Preview]: Soft delete should be enabled for Recovery Services Vaults built-in policy
- Added the [Preview]: Multi-User Authorization (MUA) must be enabled for Backup Vaults. built-in policy
- Added the [Preview]: Multi-User Authorization (MUA) must be enabled for Recovery Services Vaults. built-in policy
- Added [Preview]: Azure Recovery Services vaults should disable public network access built-in policy to the "Deny-PublicPaaSEndpoints" initiative and assignment.
- Added new initiative and assignment to enable auditing for Trust Launch capable virtual machines which includes the following built-in policies:
- Updated ARM deployment for Defender for APIs, which now requires a sub plan be specified. We're defaulting to sub plan "P1", and have confirmed that costs will only be incurred once an API has expressly been onboarded to Defender for APIs. Please thoroughly review Defender for API plans as they related to your environment and adjust the sub plan as needed.
- Deprecated custom policy Storage Account set to minimum TLS and Secure transfer should be enabled and replaced with two built-in policies Secure transfer to storage accounts should be enabled and Storage accounts should have the specified minimum TLS version.
- Added new custom policy "Deploy-Private-DNS-Generic" this policy will DINE-configure private DNS zone groups to override the DNS resolution for PaaS services private endpoint. It is generic to enable private DNS zones for the services which supports private DNS but don't have built-in policies available and also for the new services which support private DNS in future. This policy also supports the configuration of the evaluation delay.
- Deprecated Deploy-EncryptTransit initiative and superseded with Deploy-EncryptTransit_20240509 to minimize breaking change impact on existing deployments.
- Fixed the assignment for Configure periodic checking for missing system updates on azure virtual machines to use the correct RBAC role.
- Added new initiative for Microsoft Defender for Endpoints Configure multiple Microsoft Defender for Endpoint integration settings with Microsoft Defender for Cloud.
Special Note: Existing consumers of ALZ will notice that some "assigned by default" initiative assignments have been replaced/renamed to avoid breaking changes to existing assignments. Therefore the below original assignments will need to be deleted, and have the new version assigned instead:
| Initiative | Display Name | Original Assignment Name | New Assignment Name | Scope of Assignment |
|---|---|---|---|---|
| Deploy-MDFC-Deploy | Deploy Microsoft Defender for Cloud configuration | Deploy-MDFC-Deploy | Deploy-MDFC-Config-H224 | Intermediate Root Management Group |
| Deploy-EncryptTransit | Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit | Enforce-TLS-SSL | Enforce-TLS-SSL-H224 | Landing Zones Management Group |
| Deploy-Diagnostics-LogAnalytics | Deploy Diagnostic Settings to Azure Services | Deploy-Resource-Diag | Deploy-Diag-Logs | Intermediate Root Management Group |
- Archived the readme content in the eslzArm folder as it is no longer relevant. Please refer to the ALZ Wiki for the latest information on how to deploy Enterprise-Scale Landing Zones. To view the content that was previously here, refer to the archive.
- Added new instructions for deploying hub and spoke network topology in multiple regions.
- Added new instructions for deploying additional vWAN hubs in multiple regions.
- Added functionality to deploy platform resources into multiple regions. In the Core settings, you will have the option to deploy resources in a secondary region. If you select Yes you will have new options:
- In the Networking topology and connectivity tab:
- If you select Hub and spoke with Azure Firewall you will deploy a second hub in a secondary region. You can configure the IP space, VPN Gateway settings, ExpressRoute Gateway settings, and Azure Firewall settings for this region. Both of the hubs will be peered, with routing for the hubs to the Azure Firewalls being deployed. If you select DDoS protection or to select the creation of Azure Private DNS Zones, these will be linked to the second hub as well.
- If you select Hub and spoke with your third-party NVA you will deploy a second hub in a secondary region. You can configure the IP space, VPN Gateway settings, and ExpressRoute Gateway settings for this region. Both of the hubs will be peered, but no routing configured. If you select DDoS protection or to select the creation of Azure Private DNS Zones, these will be linked to the second hub as well.
- If you select Virtual WAN you will deploy a second virtual hub in a secondary region, as part of your virtual WAN deployment. You can configure the IP space, VPN Gateway settings, ExpressRoute Gateway settings, and Azure Firewall settings for this region. Both of the hubs will be peered, with routing for the hubs to the Azure Firewalls being deployed.
- In the Identity tab, if you have selected a topology to deploy, you will have the option to deploy an Identity virtual network to the secondary region, peered to the hub in that region.
- In the Networking topology and connectivity tab:
- Add additional, optional, telemetry to help the ALZ team identify styles of deployments.
- Added new AMA Policies and Initiatives to ALZ Policies documentation.
- Updated community call wiki page with links for March 2024 recording and slides.
- Add new Regulatory Compliance Policy Assignment flexibility feature
- Added ARM template to enable Microsoft Defender for Cloud as part of the deployment. Policies will still remediate additional subscriptions added to ALZ after deployment.
- Resolved an issue that prevented the policy remediation from working properly for VM Insights, Change Tracking, Azure Update Manager policies. The root cause was a too restrictive access configuration for the Managed Identity that performs the remediation tasks.
-
New deployments will now:
- Add an additional role assignment for VMInsights Policies that are assigned at Landing Zone management group scope, granting the Managed Identity the Reader role on the Platform management group.
- Add an additional role assignment for ChangeTracking Policies that are assigned at Landing Zone management group scope, granting the Managed Identity the Reader role on the Platform management group.
- Add an additional role assignment to Azure Update Manger Policies, granting Managed Identity Operator at the same scope as the assignment.
-
To update an existing deployment:
-
This script Set-RBACAmaPolicyAssignment.ps1 will update the required role assignments. The
enterpriseScaleCompanyPrefixparameter is required for running the script and should contain the intermediate root management group name..\Set-RBACAmaPolicyAssignment.ps1 -enterpriseScaleCompanyPrefix contoso
-
-
New deployments will now:
- Disabled a Policy in the Microsoft Defender for SQL initiative. As it is not required at this stage. See ALZ AMA FAQ for more details.
- Changed enforcementMode of the assignment of Policy "Deploy-UserAssignedManagedIdentity-VMInsights" to Default. This is to ensure that a Resource Group and a User Assigned Managed Identity are created on new subscriptions (subscriptions that are added after the initial deployment).
- Bug fix for Portal Accelerator. userAssignedIdentityResourceGroup has been added as output for the Portal UI, this fixes deploying the Resource Group with a custom name.
- Bug fix for Portal Accelerator.
subscriptionIdsnow uses lambda function to obtain the subscription IDs fromcorpConnectedLzSubscriptionId. This fixes the Invalid Template error when selecting a corp connected landing zone deployment. - Bug fix for Portal Accelerator.
connectivitySubscriptionIdis now skipped when no networking components are deployed. This fixes an InvalidTemplateDeployment error deploying the Resource Group for UAMI. - From Portal Accelerator: removed the options to select VM vulnerability assessment provider and to select Defender for Cloud for DNS. These are now default to the recommended settings.
The Azure Monitor Agent (AMA) is the new way to collect and send data to Azure Monitor. The Log Analytics agent, or the Microsoft Monitoring Agent (MMA), will no longer be supported after August 2024. To adapt to this change, the ALZ Portal Accelerator has been updated to use AMA instead of MMA.
This update currently applies to Greenfield Portal Deployment Scenarios. Brownfield guidance as well as Bicep and Terraform updates to follow in short-term.
We are happy to announce that we have added a new section in the documentation for AMA. Please visit ALZ AMA Update for a detailed overview of the changes made to the ARM templates and Policies, as well as the deprecated policy assignments.
IMPORTANT We've added an ALZ AMA FAQ with important information about key changes in AMA. Please read the ALZ AMA FAQ for more information.
Yes, the Q2 Policy Refresh has been delayed due to a light past quarter and some very important initiatives that we feel had to make it into this refresh.
IMPORTANT We've updated the ALZ Policy FAQ with important information about the new Diagnostic Settings v2 policies and initiatives that are will be landing soon. Please read the ALZ Policy FAQ and Tips for more information.
- Added built-in policy to Deploy-MDFC-Config initiative and default assignment to Setup subscriptions to transition to an alternative vulnerability assessment solution. This policy will enable the Microsoft Defender for Endpoint Threat Vulnerability solution on all virtual machines in all subscriptions, which is free to all Azure subscribers. This is implemented as the Qualys based solution is retiring on 1 May, 2024. For more information, please see the Microsoft Defender for Cloud documentation.
- VM vulnerability scanning will be enabled by default at subscription level as there is no cost and it is best practice.
IMPORTANT Take special note of additional steps, in the docs page listed above, that are required to offboard the legacy Qualys solution from your environment.
- 🎉 Added new initiative default assignment at the Intermediate Root Management Group for Resources should be Zone Resilient in Audit mode.
- Added new default assignment at the Intermediate Root Management Group for Resource Group and Resource locations should match, which will help customers better manage and identify regionally deployed resources and ultimately support improved resilience.
- We are deprecating MariaDB custom policies. For more information: ALZ Policies FAQ
- Fixed a typo in the Private DNS Zones initiative for the policy definition IDs for Databrics (corrected to Databricks). While not a breaking change, it is recommended to redeploy the initiative to ensure the correct policy definition IDs are used if you are using Private DNS Zones for Databricks - specifically if you have configured any exclusions or overrides for the Databricks policy definitions, as these rely on the policy definition ID (which has been updated). You will need to recreate the exclusions or overrides for Databricks if you choose not to redeploy the initiative.
- Added 'Container Apps environment should disable public network access' to 'Deny-PublicPaaSEndpoints'.
- Added 'Container Apps should only be accessible over HTTPS' to this 'Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit'.
- Bug fix for Portal Accelerator, removing region restrictions for VPN Gateways when deploying regional (not AZ).
- Bug fix for Portal Accelerator deployment when deploying using a single platform subscription. Previously, a single tenant deployment would have three failed deployments for diagnostic settings which were looking for non-existent management groups (Management, Identity and Connectivity). This has been fixed and the deployment will now succeed.
- Added drop down selection option for Azure Private Link Private DNS Zones as part of portal based ALZ deployment experience where you can select to deploy or not to deploy a subset of Private Link Private DNS zones.
- Updated ALZ policy testing framework on pull request to only test new or changed policies, drastically speeding up the testing process.
- Updated broken links in Deploying ALZ ZT Network
- Added wiki document for recommended Resource Providers to register for Subscriptions in ALZ ALZ Azure Resource Provider Recommendations
- Added a new policy/initiative submission form template for GitHub Issues. This will help us to better understand the policy/initiative you are submitting and will help us to review and approve the submission faster. Please use this template when submitting new policies/initiatives to the ALZ GitHub Issues page.
- Added new section to the ALZ Wiki FAQ to provide guidance around Private DNS Zone/Privatelink issues - read here.
- December 6th External Community Call recording and slides published to aka.ms/alz/community
- Added virtual hub routing preference support to Portal Accelerator for scenarios where you need to influence routing decisions in virtual hub router towards on-premises. For existing ALZ customers please visit Configure virtual hub routing preference for details on how to configure virtual hub routing preference settings.
- Added virtual hub capacity option to Portal Accelerator which provides an option to select the number of routing infrastructure units. Please visit Virtual hub capacity for more details on Azure vWAN Virtual Hub Capacity configuration.
- Fixed a bug in the portal accelerator experience when deploying with single platform subscription and selecting virtual WAN networking topology - Invalid Template error.
- Updated the ALZ Portal Accelerator and default assignments for Microsoft Defender for Cloud (MDFC) VM Vulnerability Assessment provider to default to use the PG recommended Microsoft Defender for Endpoint Threat/Vulnerability Management (mdeTVM) provider, instead of the Qualys provider.
- Fixed in ALZ Azure Setup the bash command to assign at root scope Owner role to a Service Principal.
- Added a new section to describe ALZ Policy Testing Framework for ALZ custom policies Policies Testing Framework.
- Added 'Container Apps environment should disable public network access' to 'Deny-PublicPaaSEndpoints'.
- Added 'Container Apps should only be accessible over HTTPS' to this 'Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit'.
- The portal accelerator experience has been updated to include deployment of Azure Monitor baseline alerts. Details on the policies deployed can be found here.
- Fixed issue with couple of Policy file names to align with the actual name of the policies
- Bug fix for Deploy-MDFC-Config version
- Add support to deploy ALZ Portal Accelerator into new Italy North region
- Fixed a bug in the portal accelerator experience when deploying a VPN Gateway and Azure Firewall (Basic SKU) - IP address overlap error.
- Added vWAN Hub Routing Intent support to Portal Accelerator for scenarios that include Azure Firewall deployment. For existing ALZ customers please visit How to configure Virtual WAN Hub routing intent and routing policies for details on how to add routing intent to your environment.
- Enhanced the ALZ Portal Accelerator to provide the ability to deploy the Azure VPN Gateway in Active/Active mode as per feedback from #655.
- Updated the ALZ Wiki FAQ to include a section on why we've enabled GitHub Releases - read here.
- Updated the ALZ Wiki FAQ to include a section on why some solutions may not deploy in an ALZ governed environment and how to work around it.
- Updated to the new Configure Microsoft Defender for Storage to be enabled built-in policy to the
Deploy-MDFC-Configinitiative and assignment.- Read more about the new Microsoft Defender for Storage here: aka.ms//DefenderForStorage.
- NOTE: there are additional cost considerations associated with this feature - more info.
- Added two new definitions with Deny Action feature:
DenyAction-ActivityLogSettings.jsonDenyAction-DiagnosticSettings.json
- Bug fix for missing diagnostic settings category for policy
Deploy-Diagnostics-CosmosDB - Added the Configure Azure Databricks workspace to use private DNS zones built-in policy to the "Deploy-Private-DNS-Zones" initiative and assignment.
Important: For existing ALZ deployments, you will need to redeploy the below assignments with least privilege RBAC roles, and review and remove existing service principals
Ownerrole assignments. The below list includes the scope that needs to be reviewed. For new deployments, the below assignments will be deployed with least privilege RBAC roles.
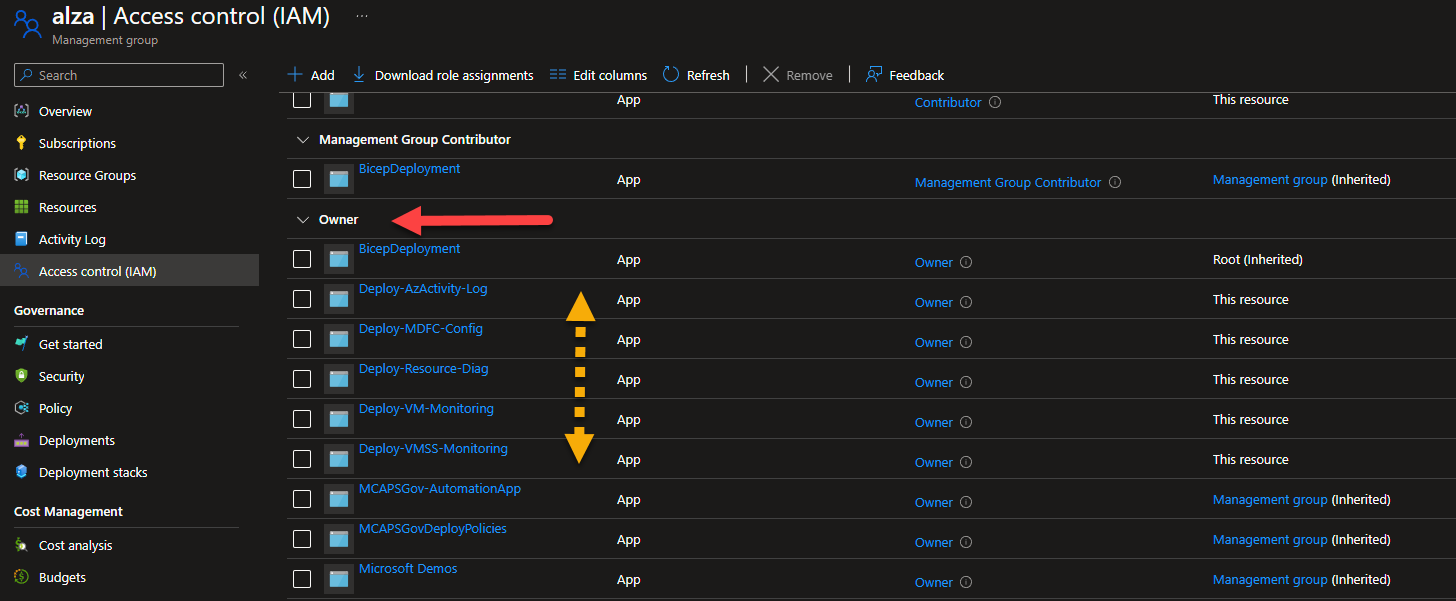
- Remediating default policy/initiative assignments using
Ownerrole to be least privilege where possible. Updated assignments:- Deploy-AzActivity-Log (Management Group: Intermediate Root)
- Deploy-AKS-Policy (added additional required role)
- Deploy-Resource-Diag (Management Group: Intermediate Root)
- Deploy-SQL-TDE (Management Group: Landing Zone)
- Deploy-VM-Backup (Management Group: Landing Zone)
- Deploy-VM-Monitoring (Management Group: Intermediate Root)
- Deploy-VMSS-Monitoring (Management Group: Intermediate Root)
- Updating custom policies using over permissive roles (Owner) to use resource scoped roles (e.g., Storage Account Contributor, Azure SQL Contributor, etc.):
- Deploy-Storage-sslEnforcement
- Deploy-SqlMi-minTLS
- Added evaluationDelay as provisioning takes around 4 hours and policy remediation fails on create due to time outs (as it normally triggers after 10 minutes).
- Deploy-SQL-minTLS
- Deploy-MySQL-sslEnforcement (changed from Owner to Contributor role, no built in roles currently available)
- Deploy-PostgreSQL-sslEnforcement (changed from Owner to Contributor role, no built in roles currently available)
- Updated to the new Configure Microsoft Defender for Storage to be enabled built-in policy to the
Deploy-MDFC-Configinitiative and assignment.- Read more about the new Microsoft Defender for Storage here: aka.ms//DefenderForStorage.
- NOTE: there are additional cost considerations associated with this feature - more info.
- Renamed Azure Active Directory to Microsoft Entra ID
Major update in this release: introducing the Policy Testing Framework foundation, along with tests for all assigned infrastructure policies that use the DENY effect. This will allow us to test the policies in a more automated fashion, and will help us to ensure that we don't introduce any regressions in the future and maintain a higher level of quality for our policies. We will be adding additional tests for custom policies in the future.
- Added additional initiative assignment for Enforce-Guardrails-KeyVault to the Platform Management Group to improve security coverage. Initially this assignment was only applied to the Landing Zone Management Group.
- Update Portal RI to include the new assignment option for the Key Vault initiative under Platform Management.
- Added new custom policy to audit Virtual Machines not using Azure Hybrid Benefit (Audit-AzureHybridBenefit)
- Fixing bug in Deploy-Sql-vulnerabilityAssessments to achieve compliance if successfully remediated. NOTE: Due to the need to change parameters, this is a breaking change. The original policy will remain in place but will be deprecated and a new policy will be deployed for the fix Deploy-Sql-vulnerabilityAssessments_20230706 - please update assignments accordingly - many thanks @Matt-FFFFFF.
- Bug fix for Management port access from the Internet should be blocked not enforcing deny effect when a deployment includes rules defined in network security group properties (i.e., when specifying rules when creating the NSG) - many thanks to @DavidRobson.
- QoL updates: adding supersededBy metadata and adding links in the description to deprecated custom policies to point to the superseding policy - aligned with ALZ specific feature updates in AzAdvertizer.
- Policy Testing Framework implemented for custom ALZ DENY policies (See Tooling section below).
- Enhanced the Azure Firewall Basic experience in the ALZ Portal Accelerator based on feedback from #1370 by removing the DNS proxy option when selecting the
BasicSKU - Updated Sentinel deployment to use new simplified pricing tier
- Established a Policy Testing Framework based on Pester, built on the work done by @fawohlsc in this repo azure-policy-testing
- Updated contribution guide to include a new section to describe how to implement tooltips when adding new policies with default assignments that require updates to the portal reference implementation.
- Adding text to the ALZ-Policies wiki page to clarify that we do use preview policies as part of initiatives in some default assignments.
- Fixed default assignment for SQLEncryption (DINE-SQLEncryptionPolicyAssignment) to use the correct policy definition.
- Added new default assignment for SQLThreatDetection (DINE-SQLThreatPolicyAssignment) to use the previous policy definition from DINE-SQLEncryptionPolicyAssignment.
- Updated the assignment DINE-LogAnalyticsPolicyAssignment (Deploy-Log-Analytics) to default enforcement mode to "DoNotEnforce". The Log Analytics workspace is deployed directly by the reference implementations, and as a result this policy is no longer required to deploy the Log Analytics workspace. Retaining the assignment for auditing purposes.
- Added new custom policies for (many thanks @jeetgarg):
- Storage Accounts with custom domains assigned should be denied - Deny-StorageAccount-CustomDomain
- File Services with insecure Kerberos ticket encryption should be denied - Deny-FileServices-InsecureKerberos
- File Services with insecure SMB channel encryption should be denied - Deny-FileServices-InsecureSMBChannel
- File Services with insecure SMB versions should be denied - Deny-FileServices-InsecureSMBVersions
- File Services with insecure authentication methods should be denied - Deny-FileServices-InsecureAuth
- 'User Defined Routes with 'Next Hop Type' set to 'Internet' or 'VirtualNetworkGateway' should be denied'
- 'Storage Accounts with SFTP enabled should be denied'
- 'Subnets without Private Endpoint Network Policies enabled should be denied'
- Updated Portal Accelerator tooltips to provide more relevance and links to associated policies or initiatives.
- When the option to deploy Log Analytics workspace and enable monitoring is enabled (Yes) in the Platform management, security, and governance section, Diagnostic Settings for Management Groups are also deployed.
- Updated
Deploy-Diagnostics-APIMgmt.jsonto support resource-specific destination table in the diagnostic setting for API Management. - Updated
Deploy-Diagnostics-LogAnalytics.jsonpolicy initiative with new parameter to support resource-specific destination table in the diagnostic setting for API Management. - Updated
Deploy-Diagnostics-Firewall.jsonto support resource-specific destination table in the diagnostic setting for Firewall - Updated
Deploy-Diagnostics-LogAnalytics.jsonpolicy initiative with new parameter to support resource-specific destination table in the diagnostic setting for Firewall - Updated
Deploy-Diagnostics-APIMgmt.jsonto support resource-specific destination table in the diagnostic setting for API Management - Updated
Deploy-Diagnostics-LogAnalytics.jsonpolicy initiative with new parameter to support resource-specific destination table in the diagnostic setting for API Management - Bug fix for
effectfor the Key Vault setting (incorrect case) inDeploy-MDFC-Config.jsoninitiative. - Bug fix for Management port access from the Internet should be blocked when a destination port array is submitted that contains port ranges that includes a denied port (22, 3389, and any others) when creating new NSG rules.
- Bug fix for AppService append sites with minimum TLS version to enforce. where the policy was preventing the creation of connection strings via API. The fix revises the policy rule logic to address the blocking issue.
- Fixed minor grammatical errors in two policy assignments.
- Deprecated policy
Deny-MachineLearning-PublicNetworkAccess. - Update initiative
Deny-PublicPaaSEndpointsto replace deprecated policyDeny-MachineLearning-PublicNetworkAccesswith builtin438c38d2-3772-465a-a9cc-7a6666a275ce. - Deprecated policy
Deny-PublicEndpoint-MariaDB. - Update initiative
Deny-PublicPaaSEndpointsto replace deprecated policyDeny-PublicEndpoint-MariaDBwith builtinfdccbe47-f3e3-4213-ad5d-ea459b2fa077- special note: US Gov/Fairfax still uses the now deprecated policy as the builtin is not yet available. - Standardized denied network resources in policy assignments for Corp and Sandbox management groups as per GH #1333.
- Added non-compliance message to
Enforce-ALZ-Sandboxinitiative assignment.
- Updated wiki deployment guides for the four main scenarios to include the new Decommissioned and Sandbox step in the portal accelerator.
- Updated ALZ Policies wiki to make the link to the Excel spreadsheet more prominent.
- Updated ALZ Policies wiki images to reflect policy initiative assignments now included for Decommissioned and Sandbox management groups.
- Updated the ALZ Policy Assignments Excel spreadsheet to include a release version column so users can track when those policies last changed and verified all assignments have a relevant AzAdvertizer link for policy details.
- Azure Enablement Show: Updating your Azure landing zones published
- Tech Community Blog: Azure Monitor Baseline Alerts (Preview) published
- Updated wiki documentation to so reflect the removal of the "Platform DevOps and automation" section from ALZ Portal Accelerator
- Added support for Azure Firewall Basic SKU to Hub & Spoke and Virtual WAN deployments in the ALZ Portal Accelerator
- Updated wiki documentation towards Subscription Vending approach for landing zone (subscription) creation
- A brand new ALZ Policy FAQ and Tips page has been added to the wiki to help answer some of the most common questions and provide some useful tips for working with ALZ policies.
- Updated ALZ Contribution Guide to include new section on how to contribute to ALZ policies resulting in breaking changes, and some minor refactoring to make it more readable.
- ALZ Bicep
v0.14.0released - ALZ Terraform (
caf-enterprise-scale)v4.0.0released - ALZ Portal Accelerator: "Platform DevOps and automation" section removed
- Removed resources from
workloadsfolder and redirected to Azure Architectures Center page of Deploy Azure landing zones
We are pleased to announce that we are starting regular Azure Policy reviews for Azure Landing Zone. This includes a review of new built-in policies released and their suitability for ALZ, built-in policies that can replace custom ALZ policies, built-in policies that have been deprecated and addition of new ALZ custom policies and initiatives as identified based on best practices, issues raised and customer feedback. Most importantly, we have also provided default assignments for all the new policies at the appropriate ALZ Management Group level. This will ensure that all new policies are automatically assigned to the appropriate scope and will be in compliance with the ALZ baseline. This will also ensure that the ALZ is always up to date with the latest Azure Policy definitions.
This update includes many ALZ Azure Policies and Initiatives that have been added or updated to enhance the security, governance, and management of ALZ. As part of our commitment to continuous improvement, we have also enhanced our policy review process, with a focus on transitioning away from deprecated policies where possible, move from custom to built-in policies providing the same or enhanced functionality, and implementing new policies to keep ALZ as part of the current review cycle. We have also implemented non-compliance messages where supported to provide a better user experience when a policy is non-compliant.
This is the first major review and refresh of Azure Policy since ALZ was GA'd. Since GA many new built-in policies and initiatives have been released which has driven the need for this review. We believe that a regular review cycle will allow us to stay on top of emerging trends and new policies, ensuring that our Azure environment remains secure and compliant. Should you identify policies or initiatives that should be considered for ALZ, kindly submit an GitHub issue. For more information, please refer to the ALZ Policies or the new Excel spreadsheet version.
We strongly advise staying up-to-date to ensure the best possible security posture for your Azure environment, see Keep your Azure landing zone up to date. For those with existing deployments or policies, we have provided Brownfield guidance to help you navigate the process of updating to the latest policies. We recognize that there may be breaking changes when upgrading an existing deployment or policies and for details follow our recently released guidance to support you in this process:
- Update Azure landing zone custom policies
- Migrate Azure landing zone policies to Azure built-in policies
Please note that, in some cases, moving to the new Built-In Policy definitions, deploying changes to existing custom policies or removing deprecated policies will require a new Policy Assignment and removing the previous Policy Assignment, which will mean compliance history for the Policy Assignment will be lost. However, if you have configured your Activity Logs and Security Center to export to a Log Analytics Workspace, Policy Assignment historic data will be stored here as per the retention duration configured. Thank you for your cooperation, and we look forward to continuing to work with you to ensure the security and compliance of our Azure environment. While we've made every effort to test the stability of this release, should you have any issues and the guidance provided does not resolve your issue, please open a GitHub issue so we can do our best to support you and document the fix for others.
Note that a number of initiatives have been updated that will fail to deploy if you have existing deployments. This is due to the fact that the number of parameters and default values have changed, as we've added or removed policies from the initiative. To resolve this, you will need to remove the existing initiative assignments and then redeploy the updated initiative.
| Initiative Name | Change | Recommended Action |
|---|---|---|
| Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit (azadvertizer.net) | Removed a deprecated policy, superceding policy is already in the initiative | Remove existing initiative assignment, delete the custom initiative and remove the orphaned identity. Deploy the updated initiative. |
- New Initiative for the Decommissioned landingzones including policies:
- Initiative name:
Enforce-ALZ-Decomm- Allowed resource types - resources are not allowed to be deployed, however, authorization, lock and tag management are permitted.
- New policy to deploy an auto shutdown policy for virtual machines - Deploy-Vm-autoShutdown
- Portal accelerator updated with additional tab and options to enable this initiative.
- Initiative name:
- New Initiative for the Sandboxes landingzones including policies:
- Initiative name:
Enforce-ALZ-Sanbox- Not allowed resource types - blocking the deployment of ER/VPN/vWAN
- Deny vNet peering cross subscription.
- Portal accelerator updated with additional tab and options to enable this initiative.
- Initiative name:
- Added initiative assignment [Preview]: Deploy Microsoft Defender for Endpoint agent to 'Intermediate Root' Management Group.
- Added assignment of Network interfaces should not have public IPs built-in Policy to the 'Corp' Management Group.
- Added new initiative and assignment to implement recommended guardrails for Azure Key Vault at the landing zones management group
- Initiative name:
ENFORCE-Guardrails-KeyVault - Policies included: ALZ Polices
- Portal accelerator updated
- Initiative name:
- Added two new policy assignments to govern Corp Management Group networking:
-
DENY-HybridNetworking- blocks the provisioning of vWAN/ER/VPN, including gateways, in Corp -
AUDIT-PeDnsZones- audits the provisioning of Private Link Private DNS Zones in Corp- NOTE: The policy default values include all the static Private DNS Zones only. When assigned via the ALZ portal experience the assignment includes all the Private DNS Zones that are deployed as part of the ALZ Portal experience, including the geo code/regional zones for Azure Backup, AKS etc.
-
- Added new policy assignment to audit WAF enabled on Application Gateways (
Audit-AppGW-WAF) - Added new initiative and assignment to enable Azure Compute Security Baseline compliance auditing for Windows and Linux virtual machines (
Enforce-ACSB) - Added new Diagnostic setting category for Host Pools Diagnostic Settings to
Deploy-Diagnostics-WVDHostPoolsConnectionGraphicsData
- Added new Diagnostic setting category for EventGrid Topics Diagnostic Settings to
Deploy-Diagnostics-EventGridTopicDataPlaneRequests
- Added two new policy initiative assignments to enable Advanced Threat Detection for databases at intermediate root:
- Add new Azure Policy Initiative and assignment (Audit-UnusedResourcesCostOptimization), at the intermediate root management group (e.g.
contoso), to audit unused resources that are driving costs. - Added new assignment to deny deployment of virtual machines and virtual machine scale sets using unmanaged OS disks.
- Added a policy assignment to deny Classic resources at the
Intermediate Rootmanagement group
- Removed deprecated policy [Deprecated]: Latest TLS version should be used in your API App (azadvertizer.net) from initiative Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit (azadvertizer.net) as recommended policy is already included in the initiative.
-
BREAKING CHANGE (parameters changed):
- Delete assignment Deny or Deploy and append TLS requirements and SSL enforcement on resources without Encryption in transit (azadvertizer.net).
- Delete custom initiative prior to applying updates as parameters have changed, then re-assign.
- Delete orphaned indentity on Landing Zone scope.
- Deploy new initiative on Landing Zone scope.
-
BREAKING CHANGE (parameters changed):
- Updated initiative Deny or Audit resources without Encryption with a customer-managed key (CMK) (azadvertizer.net) deprecated policy [Deprecated]: SQL servers should use customer-managed keys to encrypt data at rest to new policy Azure Policy definition SQL servers should use customer-managed keys to encrypt data at rest
- Updated initiative and assignment Deploy Microsoft Defender for Cloud configuration to include the new policies:
- [Preview]: Configure Microsoft Defender for APIs should be enabled
- Configure Microsoft Defender CSPM to be enabled
- Configure machines to receive a vulnerability assessment provider
- Deploy Azure Policy Add-on to Azure Kubernetes Service clusters
- Configure Azure Kubernetes Service clusters to enable Defender profile
- Replaced policy assignment "Auditing on SQL server should be enabled" with "Configure SQL servers to have auditing enabled to Log Analytics workspace" on
Landing ZonesManagement Group, to suitably assign respective DINE policy definition, instead of AINE - Deprecated
Deny-RDP-From-Internetand added new policyDeny-MgmtPorts-From-Internetwhich is more flexible and blocks port 22 and 3389 by default - Updated the initiative
Deny-PublicPaaSEndpointsto include additional policies available to block public access for PaaS services - Added new policy to initiative that enables diagnostic settings for VWAN S2S and added as part of diagnostic settings policy initiative.
- Updated ALZ Policies wiki:
- Removed the "Version" column to improve readability.
- Added the option to download an Excel file with all the policy/initiative assignments.
- Update ALZ Policies wiki: Excel file with all the policy/initiative assignments.
- Renamed Policies from
WVDtoAVD- Display names and Descriptions only - Update the
Deploy SQL Database built-in SQL security configurationinitiative to point to the built-in policy Deploy SQL DB transparent data encryption instead of the deprecated custom policyDeploy SQL Database built-in SQL security configuration. - Update policy Append-Redis-disableNonSslPort: remove not applicable 'modify' effect.
- Update ALZ Policies Wiki to include guidance around the use of managed identities with the ALZ Policy Initiative.
- Deprecated the custom ALZ policy
Deploy SQL Database Transparent Data Encryptionas there is now a built-in policy available in Azure Policy Deploy SQL DB transparent data encryption. - No longer assign Databricks custom policies at
Corpmanagement group scope. Policies:- Deny-Databricks-NoPublicIp
- Deny-Databricks-Sku
- Deny-Databricks-VirtualNetwork
If you are not using these policies, we advise you remove the assignment at
Corpmanagement group level, if you are not utilizing them.
- FIX: Updated the Fairfax (US Gov) portal accelerator experience so it now works as expected.
- Service Map solution has been removed as an option to be deployed, as this has been superseded by VM Insights, as documented here. Guidance on migrating and removing the Service Map solution can be found here.
- Added new question and answer to FAQ for "Why hasn't Azure landing zones migrated to the Azure Monitor Agent yet?"
- Published new CAF docs for Azure landing zones and multiple Microsoft Entra tenants - aka.ms/ALZ/MultiTenant
- Added additional deployment telemetry collection data point for Zero Trust Networking intent as documented here.
- Defaulted Azure Firewall SKU/Tier to
PremiumfromStandard. SKU/Tier can still be set back toStandardif desired
- Updated
Deploy-Diagnostics-Databricks.jsonpolicy with missing log categories - Updated
Deploy-Diagnostics-PostgreSQL.jsonpolicy to include setting Diagnostic Settings on PostgreSQL flexible server - Updated
Deploy-Diagnostics-Website.jsonpolicy to set Diagnostic Settings based on the AppService plan, as the Premium Tier has more categories available. - Removed duplicated category entry from
Deploy-Diagnostics-VNetGW.jsonpolicy.
- Added note to the portal experience on the "Platform DevOps and automation" blade warning that a management/platform subscription must be selected otherwise the blade will be blank
- Updated
Deploy-SQLVulnerabilityAssessments.jsonpolicy to use Storage Account Contributor for storing the logs. - Updated the same policy parameter description for email recipients explaining string type and how to format input.
- Fix typo in Deny-MachineLearning-PublicAccessWhenBehindVnet.json.
- ALZ External Community Call held. Recording and slides can be found here.
- Migrated the following pages to the Enterprise-Scale Wiki
- Updated the guidance for contributing to the Azure/Enterprise-Scale repository
- Updated "Deploy Diagnostic Settings to Azure Services" initiative replacing deprecated policy for diagnostic settings on Storage Account
- Removed all exclusions (parameters) from the Microsoft Cloud Security Benchmark (currently Azure Security Benchmark) initiative assignment to standardize across reference architectures and align with best practice. Impacted assignment: Deploy-ASC-Monitoring
- Updated "**Deploy Diagnostic Settings for Data Factory to Log Analytics workspace" to include new categories of:
SandboxPipelineRuns&SandboxActivityRuns - Add missing
minimalSeverityparameter toDeploy-ASC-SecurityContactsPolicy Definition
- Removed
ActivityLogSolution as an option to be deployed into the Log Analytics Workspace. As this has been superseded by the Activity Log Insights Workbook, as documented here.
- Renamed Azure DDoS Standard Protection references to Azure DDoS Network Protection.
- Added ALZ deprecated policies section to the Wiki.
- Included documentation on how to Migrate ALZ custom policies to Azure builtin policies to the Wiki.
- Added links to the superseding policies on the ALZ Deprecated Services page.
- Renamed Azure Security Benchmark references to Microsoft Cloud Security Benchmark.
- Updated ALZ Portal Accelerator to support all available Availability Zones as listed here
- Update ALZ Portal Accelerator Private DNS Zones for Private Link, fixing issue #1073
-
"Deploy Diagnostic Settings for Log Analytics to Log Analytics workspace" definition added and also added to
Deploy-Diagnostics-LogAnalyticsinitiative -
"Deploy Diagnostic Settings for Databricks to Log Analytics workspace" definition update
- Version 1.1.0 -> 1.2.0
- Added missing log categories
-
"Deploy SQL Database security Alert Policies configuration with email admin accounts" definition update
- Version 1.0.0 -> 1.1.1
- Changed email addresses from hardcoding to array parameter
-
"Deploy SQL Database Transparent Data Encryption" definition update
- Version 1.0.0 -> 1.1.0
- Added system databases master, model, tempdb, msdb, resource to exclusion parameter as default values
- Added as Policy Rule 'notIn' which will exclude the above databases from the policy
-
Updated "Deploy-Private-DNS-Zones" Custom initiative for Azure Public Cloud, with latest built-in Policies. Policies were added for the following Services:
- Azure Automation
- Azure Cosmos DB (all APIs: SQL, MongoDB, Cassandra, Gremlin, Table)
- Azure Data Factory
- Azure HDInsight
- Azure Migrate (missing Private DNS Zone also added)
- Azure Storage (Blob, Queue, File, Static Web, DFS and all relative secondaries)
- Azure Synapse Analytics
- Azure Media Services
- Azure Monitor
-
Minor fixes related to "Deploy-Private-DNS-Zones" Custom Initiative and respective Assignment:
- Added missing Zones for "WebPubSub" and "azure-devices-provisioning", so Initiative Assignment works correctly
- Minor correction related to ASR Private DNS Zone variable, so Initiative Assignment works correctly
- Conversion of "Azure Batch" Private DNS Zone (from regional to global), to properly align with latest respective documentation and functionality
-
Renamed Azure DDoS Standard Protection references to Azure DDoS Network Protection.
-
Incremented version for policy Deploy-DDoSProtection from "version":"1.0.0" to "version": "1.0.1"
-
Added
Configure Microsoft Defender for Azure Cosmos DB to be enabledto theDeploy Microsoft Defender for Cloud configurationinitiative and updated version to3.1.0- Fixing issue issue #1081 -
Added
AZFWFlowTracecategory for Azure Firewall in associated Diagnostic Policy -
Deprecated the following ALZ policies
in favour of Azure built-in policies with the same or enhanced functionality.
| ALZ Policy ID(s) | Azure Builti-in Policy ID(s) |
|---|---|
| Deploy-Nsg-FlowLogs-to-LA | e920df7f-9a64-4066-9b58-52684c02a091 |
| Deploy-Nsg-FlowLogs | e920df7f-9a64-4066-9b58-52684c02a091 |
| Deny-PublicIp | 6c112d4e-5bc7-47ae-a041-ea2d9dccd749 |
-
""Deploy-ASC-SecurityContacts"" definition update
- displayName and description update to "Deploy Microsoft Defender for Cloud Security Contacts"
- Added new parameter
minimalSeveritywith settings- Default value
High - Allowed values:
High,Medium,Low
- Default value
-
""Deploy-MDFC-Config"" definition update
- Updated policy definitions set Deploy-MDFC-Config, Deploy-MDFC-Config(US Gov), Deploy-MDFC-Config (China)
- added new parameter
minimalSeverity. - added default value for multiple parameters.
- added new parameter
- Updated policy definitions set Deploy-MDFC-Config, Deploy-MDFC-Config(US Gov), Deploy-MDFC-Config (China)
- No updates, yet.
- Added 2 new FAQ Q&As based on issue #1080
- Release
v2.4.1of the Azure landing zones Terraform module adds a new diagnostic category for Azure Firewall, as reported in issue #1063 - Update the Azure landing zone portal accelerator to use Resource Graph with a generic drop down UI element to improve user experience for subscription selection.
- Update the Azure landing zone portal accelerator to have more unique naming for deployment names in same tenant, using
utcNow()function indeploymentSuffixvariable - fixes #1077 - Update the Azure landing zone portal accelerator to have more unique naming for vNet names - fixes #881
- vNet naming pattern changed:
-
From:
- Identity vNet:
<Subscription ID>-<Root ID Prefix>-vnet-<Region Short Name> - Corp vNets:
<Subscription ID>-<Root ID Prefix>-vnet-<Region Short Name>
- Identity vNet:
-
To:
- Identity vNet:
<Root ID Prefix>-vnet-<Region Short Name>-<Subscription ID>(then trimmed to 64 characters, usingtake()function, starting at front - so Subscription ID will get trimmed) - Corp vNets:
<Root ID Prefix>-vnet-<Region Short Name>-<Subscription ID>(then trimmed to 64 characters, usingtake()function, starting at front - so Subscription ID will get trimmed)
- Identity vNet:
-
From:
-
⚠️ This is a breaking change, only if you attempt to redeploy the Azure landing zone portal accelerator over the top of an existing Azure landing zone portal accelerator deployment that was deployed prior to 12/10/2022 (12th October 2022)⚠️ - The outcome if you do this will be that new vNets will be created based on what you input into the Azure landing zone portal accelerator form when you fill it out. Even if you input exactly the same inputs and details as the first time you deployed it.
- However, this is a very uncommon action and if you are impacted please raise an issue on the repo and we can assist further
- The outcome if you do this will be that new vNets will be created based on what you input into the Azure landing zone portal accelerator form when you fill it out. Even if you input exactly the same inputs and details as the first time you deployed it.
- vNet naming pattern changed:
- Release of various ALZ-Bicep versions:
- Updated Azure landing zone portal accelerator with a note around existing Management Group Name/IDs on "Azure core setup" blade linking to FAQ Q&As
- Added
Configure Microsoft Defender for Azure Cosmos DB to be enabledto theDeploy Microsoft Defender for Cloud configurationinitiative and updated version to3.1.0- Fixing issue issue #1081 - Updated the Diagnostic Settings Policies to leverage the profileName parameter properly, rather than hardcoded value (setByPolicy) - Fixing issue issue #478
- No updates, yet.
-
Updated the Enterprise-scale Wiki to reflect the latest updates on Azure landing zone accelerator.
- Release
v2.4.0of the Azure landing zones Terraform module - Updated Automation Account region mapping in the Terraform implementation option
- No updates, yet.
- No updates, yet.
- No updates, yet.
- Updated the
eslzArmimplementation (Portal accelerator) to use a newpolicies.jsonfile. This file is now programmatically generated from a library of individual resource definitions using a Bicep template, and was introduced to:- Simplify maintenance of individual policies
- Improve traceability and testability of policy changes
- Provide universal support across multiple cloud environments, including AzureCloud (public), AzureChinaCloud and AzureUSGovernment
- As a bonus, we have also improved consistency of metadata implemented across the policies
- Updated Azure Backup geo codes for new regions across ARM, Bicep and Terraform implementation options
- No updates, yet.
- No updates, yet.
- Updated the ALZ Terraform module Wiki to reflect the latest fixes.
- Various updates to CAF ALZ Docs
- Identity and Access Management
- Network Topology and Connectivity
- Management
- Platform Automation and DevOps
- ALZ Terraform module hotfix release v2.1.2, for regional private endpoint DNS zones
- ALZ Bicep modules release v0.9.2 released
- Added Landing Zone Management Group Children Flexibility
- Added Policy Assignments for Mooncake (Azure China)
- Fixed Azure Backup Private DNS Zone Geo Codes bug, fixing issue #279
- ALZ Accelerator (Portal Experience) updated to fix Azure Backup Private DNS Zone Geo Codes, fixing issue #1004
- No updates, yet.
- No updates, yet.
- Updated the Policies included in Enterprise-Scale Landing Zones page.
- Updated the ALZ Terraform module Wiki with new examples and improved coverage of variable configuration.
- Fixed issue #979 by adding support for the additional Log Analytics Solutions of
SQLVulnerabilityAssessmentandSQLAdvancedThreatProtectionto the Azure Landing Zone Accelerator (portal experience) - ALZ Terraform module minor release v2.1.0, to provide feature parity on the fix for issue #979
- ALZ Terraform module hotfix release v2.1.1 (see release notes for more information).
- Renamed Diagnostic Settings Policies from
WVDtoAVD- Fixing issue issue #962-
displayNameanddescriptionupdated only.nameleft asWVDto avoid in-place update issues for existing deployments - Add 2 new categories for Host Pools Diagnostic Settings
NetworkDataSessionHostManagement
-
- Added AVD Scaling Plans Diagnostic Settings called
Deploy-Diagnostics-AVDScalingPlansfor Azure Public only - as not supported in Fairfax or Mooncake as per https://learn.microsoft.com/azure/virtual-desktop/autoscale-scaling-plan - Fixing issue issue #962- Added to
Deploy-Diagnostics-LogAnalyticsPolicy Initiative
- Added to
- Added additional log categories to
Deploy-Diagnostics-Firewallfor Azure Firewall Diagnostic Settings Policy - Fixing issue issue #985 - Added additional log categories to
Deploy-Diagnostics-APIMgmtfor Azure API Management Diagnostic Settings Policy - Fixing issue issue #986 - Added new Policy for for Azure Bastion Diagnostic Settings Policy called
Deploy-Diagnostics-Bastion- Fixing issue issue #968- Added to
Deploy-Diagnostics-LogAnalyticsPolicy Initiative
- Added to
- Updated
Deny-MachineLearning-ComputeCluster-RemoteLoginPortPublicAccessmode fromIndexedtoAll- Fixing issue issue #978 - Updated
Deploy-Storage-sslEnforcementexistence condition - Fixing issue issue #971 - Updated
Deploy-Diagnostics-MlWorkspacemetrics and categories - Fixing issue issue #893
- No updates, yet.
- Updated the What is an Azure landing zone? page
- Updated the Azure landing zone - design principles page
- Updated the Azure landing zone design areas overview page
- Updated the Landing zone implementation options page
- Updating Azure Firewall to use Availability Zones inside of Azure Virtual WAN Secure Hub: Azure Firewall Updates and Azure Firewall with Availability Zones
- ALZ Terraform module patch release v2.0.2 - three minor bugs squashed 🐛 🐛 🐛 🥳
- No updates, yet.
- Published resources from the third Azure Landing Zones Community Call - held on the 2nd May 2022
- Meeting recording and PowerPoint slides published in Wiki
- See issue #949 for meeting details
- New CAF document Plan for virtual machine remote access
- New CAF document Use Terraform to deploy Azure landing zones
- Helps you to understand what Terraform approach and module to use to deploy, manage and operate ALZ
- New CAF document Tailor the Azure landing zone architecture to meet requirements
- Guidance to help you understand how to tailor the ALZ architecture to meet your additional requirements
- New CAF document Independent software vendor (ISV) considerations for Azure landing zones
-
Azure Landing Zones Terraform Module v2.0.0 released 🥳
- Adds support for Virtual WAN plus much more
- Checkout release notes for details on all the changes and fixes
- Checkout upgrade guide for details on how to upgrade to the latest release
- Updated Private DNS Zones that are created for Private Link/Endpoints in Portal Experience as per documentation here: Azure Private Endpoint DNS configuration
- Also fixes issue 944
- Added Telemetry to Portal Experience. More info here Telemetry Tracking Using Customer Usage Attribution (PID)
- Increase
preparingToLaunchdeployment delay in portal experience to improve scenario in issue 902 - Added warnings to use dedicated Subscriptions for platform services when selecting the dedicated model to help avoid deployment failures seen when selecting the same Subscription in the dedicated platform Subscription model for Management, Identity and Connectivity
- Improving experience as suggested in issue 910
- Customers wanting a single subscription for platform services should select the 'Single' option on the 'Azure Core Setup' blade
- Added new custom policy definition called
Deny vNet peering to non-approved vNets- This is useful in scenarios where you only want to allow vNet peering to say a central hub vNet and not allow other vNet peerings between landing zones to be enabled.
- No updates, yet.
- Added new FAQ question and answer for AzureDiagnostic table limits for Log Analytics Workspaces
- The Bicep version of Azure Landing Zone (formerly Enterprise-scale) is here! 🥳
- Check out the ALZ-Bicep repo to get started!
- Updated accelerator (portal) experience to deploy an Azure Firewall Policy
PremiumSKU instead ofStandardwhenPremiumis selected for the Azure Firewall in a Hub & Spoke VNet Connectivity model. - Updated accelerator (portal) experience to deploy an Azure Firewall Policy for customers using the Virtual WAN connectivity model.
- Renamed
Deploy-ASCDF-ConfigtoDeploy-MDFC-Configand updated version to3.0.0- fixing issue 923
- No updates, yet.
- No updates, yet.
- New release v1.1.0 of the caf-enterprise-scale Terraform module, providing updates to the published policies and a number of bug fixes.
- Updated
Deny-Subnet-Without-Nsg&Deny-Subnet-Without-Udrto version 2.0.0- Fixes scenario described in issue issue #407
- Updated
Deploy-ASCDF-Configpolicy initiative with changes relating to new Microsoft Defender for Cloud Containers plan as documented in issue #874- Updated in Public (Commercial), Fairfax (Gov) and Mooncake (China)
- Updated portal experiences for Public and Fairfax
| Policy Definition Display Name | Policy Definition ID | Note |
|---|---|---|
| [Deprecated]: Configure Azure Defender for container registries to be enabled | d3d1e68e-49d4-4b56-acff-93cef644b432 | REMOVED - Old ACR policy |
| [Deprecated]: Configure Azure Defender for Kubernetes to be enabled | 133047bf-1369-41e3-a3be-74a11ed1395a | REMOVED - Old AKS Policy |
| Configure Microsoft Defender for Containers to be enabled | c9ddb292-b203-4738-aead-18e2716e858f | ADDED - New grouped containers policy for the new plan |
- No updates, yet.
- CAF ready lots of doc updates relating to Azure Landing Zones/Enterprise Scale
- Added doc on Adopting policy driven guardrails
- Added doc called Scenario: Transition existing Azure environments to the Azure landing zone conceptual architecture
- More of these to come, let us know via issues on other scenarios you'd like to see documented
- Design Areas updated and reorganized in TOC (navigation pane)
- Updated DIY instructions for deploying Enterprise-Scale in Azure China with:
- Additional details of some deployment steps
- Microsoft Defender for Cloud configuration policy set definition and policy assignment specific to Azure China
- Differentiate between Az VM Backup policy assignment for identity management group, and landing zone management group in the DIY guidance
- The following policy definitions for Microsoft Defender for Cloud configurations are not available as built-in in Azure China. The policy set definition will be updated as when these policy definitions are available:
- defenderForOssDb, defenderForSqlServerVirtualMachines, defenderForAppServices, defenderForAppServices, defenderForStorageAccounts, defenderForKeyVaults, defenderForDns, defenderForArm
- No updates, yet.
- New release v1.1.0 of the caf-enterprise-scale Terraform module, providing updates to the published policies and a number of bug fixes.
-
Replaced
Deploy-Default-Udrpolicy withDeploy-Custom-Route-Tablethat allows deploying custom route tables with an arbitrary set of UDRs (including a 0/0 default route if needed). See here for usage details. -
Updated
Deploy-Budgetpolicy, to v1.1.0, adding new parameter ofbudgetNamethat defaults to:budget-set-by-policy- closing issue #842- Including Fairfax
- Also Mooncake (Azure China) even though not in use yet
-
Added
AuditEventtoDeploy-Diagnostics-AAPolicy Definition to ensure correct compliance reporting on Automation Account used for diagnostics - closing issue #864
- Published resources from the second Enterprise Scale Community Call - held on the 17th November 2021
- Meeting recording and PowerPoint slides published in Wiki
- See issue #803 for meeting details
- Updates to User Guide to include instructions for deploying each of the reference implementations.
- Updated Deploying Enterprise Scale wiki page with updated workflow steps. (https://github.com/Azure/Enterprise-Scale/pull/827)
- Updated implementation FAQ and moved to the Wiki
- Added architecture FAQ to the CAF docs
- Terraform Enterprise Scale Module reaches GA (V1.0.0) - see release notes
- ESLZ reference implementation updated with built-in (11) policies for Azure Security Center, enforcing (DeployIfNotExists) Azure Security Center with Standard Tier for Azure Defender for the following services:
- Kubernetes
- App Services
- VMs
- Key Vault
- Azure Resource Manager
- DNS
- Open-source relational databases
- SQL on VMs
- SQL databases
- Storage
- Container Registries
- No updates, yet.
- No updates, yet.
- Added reference to Enterprise-Scale Analytics (https://github.com/Azure/Enterprise-Scale/pull/809)
- Added Do-It-Yourself instructions for deploying Enterprise-Scale in Azure China regions (https://github.com/Azure/Enterprise-Scale/pull/802)
- Added Option to select Azure Firewall SKU (https://github.com/Azure/Enterprise-Scale/pull/793)
- AzOps release v1.5.0
- Enabled support for Enterprise-Scale landing zones deployments to Azure gov (https://github.com/Azure/Enterprise-Scale/pull/820)
| Custom ESLZ Policy Name | Custom ESLZ Policy Display Name | Custom Category | Built-In Policy Name/ID | Built-In Policy Display Name | Built-In Category | Notes |
|---|---|---|---|---|---|---|
| Deny-Databricks-NoPublicIp | Deny public IPs for Databricks cluster | Databricks | Denies the deployment of workspaces that do not use the noPublicIp feature to host Databricks clusters without public IPs. | |||
| Deny-Databricks-Sku | Deny non-premium Databricks sku | Databricks | Enforces the use of Premium Databricks workspaces to make sure appropriate security features are available including Databricks Access Controls, Credential Passthrough and SCIM provisioning for Microsoft Entra ID. | |||
| Deny-Databricks-VirtualNetwork | Deny Databricks workspaces without Vnet injection | Databricks | Enforces the use of vnet injection for Databricks workspaces. | |||
| Deny-MachineLearning-PublicNetworkAccess | Azure Machine Learning should have disabled public network access | Machine Learning | Denies public network access for Azure Machine Learning workspaces. |
- No updates, yet.
- Updated Enterprise Agreement enrollment and Microsoft Entra tenants CAF doc
- Added CSP, MCA & other billing offers
- Added information on how an EA relates to Microsoft Entra ID and ties in with RBAC
- Lots of updates to the Terraform Module for Cloud Adoption Framework Enterprise-scale wiki
-
Terraform Module for Cloud Adoption Framework Enterprise-scale release v0.4.0
- Brings support for Hub Connectivity & Identity landing zone peering - read more in the release notes linked above
- Do-It-Yourself deployment instructions for Enterprise-Scale using Azure PowerShell released
- Update subscription filter in reference implementation UI experience. Subscriptions with state != "Enabled" will be excluded from the list of available subscriptions.
- Removed old codebase for the different reference implementations, and converged to a single ARM codebase
- Improved Network CIDR Range Validation within the Azure Portal experience (https://github.com/Azure/Enterprise-Scale/pull/767).
- Some minor changes to parameters and variables, tidying up some code.
- See PR #727
- Updated policy Deploy-VNET-HubSpoke to address #726 and #728
- See PR #772
- Published resources from the first Enterprise Scale Community Call - held on the 25th August 2021
- Meeting recording and PowerPoint slides published in Wiki
- See issue #668 for meeting details
- Added guidance for Resource Group usage for Azure Networking topologies in Hub & Spoke & Virtual WAN CAF docs - closing issue #632
- Updated Connectivity to Azure PaaS services CAF docs based on customer feedback around Private Link /Service Endpoints differences and guidance, including ExpressRoute peering options relating to this. Closing issue - #519 on CAF repository
- Updated Contoso, Adventure Works & Wingtip Toys reference implementations with new Deploy To Azure buttons for new portal experience
- Also updated guidance and option availability for each of them respectively
- User Guide updated to reflect latest release and new portal experience
- New Article to Deploy Azure Red Hat OpenShift (ARO) in enterprise-scale landing zones
- Portal Experience Updated
- Merged Contoso, AdventureWorks, and Wingtip into one ESLZ deployment experience via first-party deployment in the portal ("Deploy To Azure" button) experience
- Support "N" network topologies in same experience (Hub and Spoke, Virtual WAN, Hub and Spoke with NVA)
- Added option for VNET Peering the Identity subscription's VNET to the Connectivity subscription's Hub VNET
- Added option for VNET peering Landing Zones to Connectivity subscription when Hub & Spoke is the selected topology (Virtual WAN is excluded due to concurrency issues, at this time) - closing issue #517
- Navigate policy assignment for identity, when using single vs dedicated subscriptions for platform purposes
- Optimized the execution graph
- Merged Contoso, AdventureWorks, and Wingtip into one ESLZ deployment experience via first-party deployment in the portal ("Deploy To Azure" button) experience
- Re-structured the ARM templates for all resource deployments
-
eslzArm.jsonis used to orchestrate the E2E composition of ESLZ, and subsequent resource deployments based on user input from the portal ("Deploy To Azure" button) experience - The composite ARM templates can be sequenced on their own, independently of each other (although strict sequencing is required to ensure the same outcome)
- Guidance coming soon for this
- Customers can deploy from private repository if they want to sequence at their own pace.
-
AzOps release v1.3.0AzOps release v1.3.1- AzOps release v1.4.0
- Various custom ESLZ Azure Policies have moved to Built-In Azure Policies, see below table for more detail:
You may continue to use the ESLZ custom Azure Policy as it will still function as it does today. However, we recommend you move to assigning the new Built-In version of the Azure Policy.
Please note that moving to the new Built-In Policy Definition will require a new Policy Assignment and removing the previous Policy Assignment, which will mean compliance history for the Policy Assignment will be lost. However, if you have configured your Activity Logs and Security Center to export to a Log Analytics Workspace; Policy Assignment historic data will be stored here as per the retention duration configured.
Policy Definitions Updates
| Custom ESLZ Policy Name | Custom ESLZ Policy Display Name | Custom Category | Built-In Policy Name/ID | Built-In Policy Display Name | Built-In Category | Notes |
|---|---|---|---|---|---|---|
| Deny-PublicEndpoint-Aks | Public network access on AKS API should be disabled | Kubernetes | 040732e8-d947-40b8-95d6-854c95024bf8 | Azure Kubernetes Service Private Clusters should be enabled | Kubernetes | |
| Deny-PublicEndpoint-CosmosDB | Public network access should be disabled for CosmosDB | SQL | 797b37f7-06b8-444c-b1ad-fc62867f335a | Azure Cosmos DB should disable public network access | Cosmos DB | |
| Deny-PublicEndpoint-KeyVault | Public network access should be disabled for KeyVault | Key Vault | 55615ac9-af46-4a59-874e-391cc3dfb490 | [Preview]: Azure Key Vault should disable public network access | Key Vault | |
| Deny-PublicEndpoint-MySQL | Public network access should be disabled for MySQL | SQL | c9299215-ae47-4f50-9c54-8a392f68a052 | Public network access should be disabled for MySQL flexible servers | SQL | |
| Deny-PublicEndpoint-PostgreSql | Public network access should be disabled for PostgreSql | SQL | 5e1de0e3-42cb-4ebc-a86d-61d0c619ca48 | Public network access should be disabled for PostgreSQL flexible servers | SQL | |
| Deny-PublicEndpoint-Sql | Public network access on Azure SQL Database should be disabled | SQL | 1b8ca024-1d5c-4dec-8995-b1a932b41780 | Public network access on Azure SQL Database should be disabled | SQL | |
| Deny-PublicEndpoint-Storage | Public network access onStorage accounts should be disabled | Storage | 34c877ad-507e-4c82-993e-3452a6e0ad3c | Storage accounts should restrict network access | Storage | |
| Deploy-Diagnostics-AKS | Deploy Diagnostic Settings for Kubernetes Service to Log Analytics workspace | Monitoring | 6c66c325-74c8-42fd-a286-a74b0e2939d | Deploy - Configure diagnostic settings for Azure Kubernetes Service to Log Analytics workspace | Kubernetes | |
| Deploy-Diagnostics-Batch | Deploy Diagnostic Settings for Batch to Log Analytics workspace | Monitoring | c84e5349-db6d-4769-805e-e14037dab9b5 | Deploy Diagnostic Settings for Batch Account to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-DataLakeStore | Deploy Diagnostic Settings for Azure Data Lake Store to Log Analytics workspace | Monitoring | d56a5a7c-72d7-42bc-8ceb-3baf4c0eae03 | Deploy Diagnostic Settings for Data Lake Analytics to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-EventHub | Deploy Diagnostic Settings for Event Hubs to Log Analytics workspace | Monitoring | 1f6e93e8-6b31-41b1-83f6-36e449a42579 | Deploy Diagnostic Settings for Event Hub to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-KeyVault | Deploy Diagnostic Settings for Key Vault to Log Analytics workspace | Monitoring | bef3f64c-5290-43b7-85b0-9b254eef4c47 | Deploy Diagnostic Settings for Key Vault to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-LogicAppsWF | Deploy Diagnostic Settings for Logic Apps Workflow runtime to Log Analytics workspace | Monitoring | b889a06c-ec72-4b03-910a-cb169ee18721 | Deploy Diagnostic Settings for Logic Apps to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-RecoveryVault | Deploy Diagnostic Settings for Recovery Services vaults to Log Analytics workspace | Monitoring | c717fb0c-d118-4c43-ab3d-ece30ac81fb3 | Deploy Diagnostic Settings for Recovery Services Vault to Log Analytics workspace for resource specific categories | Backup | |
| Deploy-Diagnostics-SearchServices | Deploy Diagnostic Settings for Search Services to Log Analytics workspace | Monitoring | 08ba64b8-738f-4918-9686-730d2ed79c7d | Deploy Diagnostic Settings for Search Services to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-ServiceBus | Deploy Diagnostic Settings for Service Bus namespaces to Log Analytics workspace | Monitoring | 04d53d87-841c-4f23-8a5b-21564380b55e | Deploy Diagnostic Settings for Service Bus to Log Analytics workspace | Monitoring | |
| Deploy-Diagnostics-SQLDBs | Deploy Diagnostic Settings for SQL Databases to Log Analytics workspace | Monitoring | b79fa14e-238a-4c2d-b376-442ce508fc84 | Deploy - Configure diagnostic settings for SQL Databases to Log Analytics workspace | SQL | |
| Deploy-Diagnostics-StreamAnalytics | Deploy Diagnostic Settings for Stream Analytics to Log Analytics workspace | Monitoring | 237e0f7e-b0e8-4ec4-ad46-8c12cb66d673 | Deploy Diagnostic Settings for Stream Analytics to Log Analytics workspace | Monitoring | |
| Deploy-DNSZoneGroup-For-Blob-PrivateEndpoint | Deploy DNS Zone Group for Storage-Blob Private Endpoint | Network | TBC | TBC | TBC | This policy is still rolling out to the Built-In Definitions at this time. We'll be here very soon! |
| Deploy-DNSZoneGroup-For-File-PrivateEndpoint | Deploy DNS Zone Group for Storage-File Private Endpoint | Network | TBC | TBC | TBC | This policy is still rolling out to the Built-In Definitions at this time. We'll be here very soon! |
| Deploy-DNSZoneGroup-For-KeyVault-PrivateEndpoint | Deploy DNS Zone Group for Key Vault Private Endpoint | Network | ac673a9a-f77d-4846-b2d8-a57f8e1c01d4 | [Preview]: Configure Azure Key Vaults to use private DNS zones | Key Vault | |
| Deploy-DNSZoneGroup-For-Queue-PrivateEndpoint | Deploy DNS Zone Group for Storage-Queue Private Endpoint | Network | TBC | TBC | TBC | This policy is still rolling out to the Built-In Definitions at this time. We'll be here very soon! |
| Deploy-DNSZoneGroup-For-Sql-PrivateEndpoint | Deploy DNS Zone Group for SQL Private Endpoint | Network | TBC | TBC | TBC | This policy is still rolling out to the Built-In Definitions at this time. We'll be here very soon! |
| Deploy-DNSZoneGroup-For-Table-PrivateEndpoint | Deploy DNS Zone Group for Storage-Table Private Endpoint | Network | TBC | TBC | TBC | This policy is still rolling out to the Built-In Definitions at this time. We'll be here very soon! |
| Deploy-LA-Config | Deploy the configurations to the Log Analytics in the subscription | Monitoring | Policy Removed | Policy Removed | TBC | This policy has been removed as it is handled as a resource deployment in the ARM templates, portal experience and Terraform module. |
| Deploy-Log-Analytics | Deploy the Log Analytics in the subscription | Monitoring | 8e3e61b3-0b32-22d5-4edf-55f87fdb5955 | Configure Log Analytics workspace and automation account to centralize logs and monitoring | Monitoring |
Policy Initiatives Updates
| Custom ESLZ Policy Name | Custom ESLZ Policy Display Name | Custom Category | New Policy Name/ID | New Policy Display Name | New Category | Notes |
|---|---|---|---|---|---|---|
| Deploy-Diag-LogAnalytics | Deploy Diagnostic Settings to Azure Services | N/A | Deploy-Diagnostics-LogAnalytics | Deploy Diagnostic Settings to Azure Services | Monitoring | Moved to using a mix of Built-In (as above) and custom policy definitions |
| Deny-PublicEndpoints | Public network access should be disabled for PAAS services | Network | Deny-PublicPaaSEndpoints | Public network access should be disabled for PaaS services | N/A | Moved to using Built-In policy definitions only (as above) |
| New Policy | New Policy | N/A | Deploy-Private-DNS-Zones | Configure Azure PaaS services to use private DNS zones | Network |
- Moved several of the diagnostics Policies to built-in, and updating the diagnostics Initiative
- This means there's a new resource name as update of existing one is not be allowed due to removal of parameters
- Added Policy Initiative for enforcing Private DNS Zone Association with Private Link (using built-in)
- Added Policy Initiative for denying Public Endpoints (using built-in)
- Updated description and display name for all Policy Assignments
No updates, yet.
- "What's New?" page created
- Azure DDoS Network Protection design considerations and recommendations added to CAF docs (Virtual WAN & Hub & Spoke) - closing issue #603
- Connectivity to other cloud providers CAF document released
- Testing approach for enterprise-scale CAF document released
- Updated pricing section on "What is Enterprise Scale" wiki page to provide further clarity.
- Updated DNS for on-premises and Azure resources - related to issue #609
- Update Hub & Spoke guidance related to BGP propagation on UDRs for transit connectivity - to close issue #618
- Added guidance to Management group and subscription organization - CAF Docs for Azure Subscription Policies, which allow you to control Azure Subscription Tenant transfers to/from your Microsoft Entra Tenant.
- Updated
Deny-Subnet-Without-UDRpolicy, to v1.1.0, to allow exclusion of subnets like theAzureBastionSubnet- closing issue #604- Also updated ESLZ-Policies.md with changes
- Updated
Deny-Subnet-Without-Nsgpolicy, to v1.1.0, to allow exclusion of subnets like theGatewaySubnet,AzureFirewallSubnetandAzureFirewallManagementSubnet- closing issue #456- Also updated ESLZ-Policies.md with changes
- Updated
Deny-VNet-PeeringandDeny-VNET-Peer-Cross-SubpoliciesmodetoAllfromIndexed. - closing issue #583- Also updated ESLZ-Policies.md with changes
- Contoso Reference Implementation Update - Virtual WAN Hub default CIDR changed from
/16to/23- closing issue #440
- What's New?
- Community Calls
- Frequently Asked Questions (FAQ)
- Known issues
- What is Enterprise-Scale
- How it Works
- Deploying Enterprise-Scale
- Pre-requisites
- ALZ Resource Providers Guidance
- Configure Microsoft Entra permissions
- Configure Azure permissions
- Deploy landing zones
- Deploy reference implementations
- Telemetry Tracking Using Customer Usage Attribution (PID)
- Deploy without hybrid connectivity to on-premises
- Deploy with a hub and spoke based network topology
- Deploy with a hub and spoke based network topology with Zero Trust principles
- Deploy with an Azure Virtual WAN based network topology
- Deploy for Small Enterprises
- Operating the Azure platform using AzOps (Infrastructure as Code with GitHub Actions)
- Deploy workloads
- Create landing zones (subscriptions) via Subscription Vending
- Azure Landing Zones Deprecated Services
- Azure Landing Zone (ALZ) Policies
- Policies included in Azure landing zones reference implementations
- Policies included but not assigned by default and Workload Specific Compliance initiatives
- Policies FAQ & Tips
- Policies Testing Framework
- Migrate Azure landing zones custom policies to Azure built-in policies
- Updating Azure landing zones custom policies to latest
- MMA Deprecation Guidance
- Contributing