On a Linear or Exponential Descending Sale Model, a user that mint on the last block.timestamp mint at an unexpected price.
#1275
Labels
2 (Med Risk)
Assets not at direct risk, but function/availability of the protocol could be impacted or leak value
bug
Something isn't working
M-04
primary issue
Highest quality submission among a set of duplicates
satisfactory
satisfies C4 submission criteria; eligible for awards
selected for report
This submission will be included/highlighted in the audit report
Lines of code
https://github.com/code-423n4/2023-10-nextgen/blob/8b518196629faa37eae39736837b24926fd3c07c/smart-contracts/MinterContract.sol#L530-L568
Vulnerability details
Impact
A user mint a token at an incorrect price and losing funds if he mint on the last authorized
block.timestampduring a Linear or Exponential Descending Sale Model.Proof of Concept
On a Linear or Exponential Descending Sale Model, the admin set the
collectionMintCostand thecollectionEndMintCost. In context of these sale models, thecollectionMintCostis the price for minting a token at the beginning and thecollectionEndMintCostthe price at the end of the sale.The minting methods use the function
MinterContract::getPrice()to compute the correct price at the actual timing, check the function with the branch for a Linear or Exponential Descending Sale Model:We can see that if the
collectionPhases[_collectionId].salesOption == 2(it's the number for a descending sale model), and if theblock.timestampis> allowlistStartTimeand< publicEndTime. The price is correctly computed.A little check on the
mint()function:But if the
publicEndTimeis strictly equal topublicEndTime, the returned price is thecollectionMintCostinstead ofcollectionEndMintCostbecause the logic go to the "else" branch. It's an incorrect price because it's the price at the beginning of the collection. And as you can see onmint(), a user can mint a token on the block.timestamppublicEndTime.User that mint on the last block.timstamp mint at an unexpected price and for all the minting methods which use the
getPrice()function.Logs
You can see the logs of the test with this image:
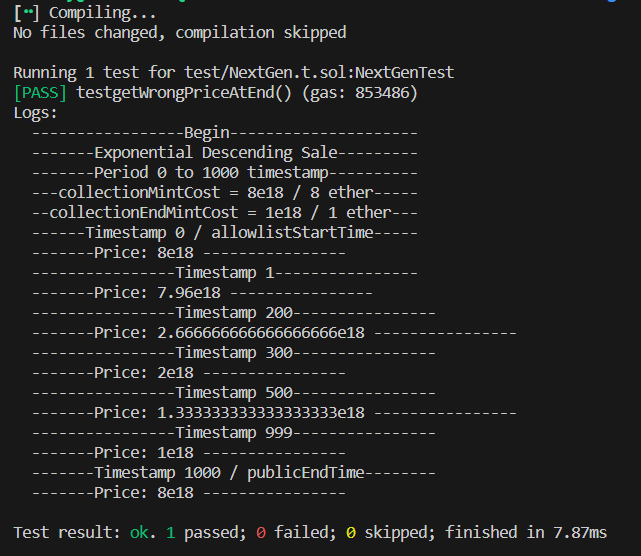
And a link of a gist if you want to execute the PoC directly.
https://gist.github.com/AxelAramburu/c10597b5ff60616b8a15d091f88de8da
And you can execute the test with this command:
Tools Used
Manual Review
Recommended Mitigation Steps
Change the
< & >to<= & =>on the else if branch inside thegetPrice()function.Assessed type
Invalid Validation
The text was updated successfully, but these errors were encountered: