-
Notifications
You must be signed in to change notification settings - Fork 22
wireshark
Econotags are easy to use as 802.15.4, Zigbee, or 6lowpan sniffers.
The firmware used to sniff 802.15.4 with Econotags is the rftest-rx program. This is part of libmc1322x. You can also buy econotags pre-programmed with this firmware from the Redwire Store.
The next step is to run the control python script, rftestrx2pcap.py, (also part of libmc1322x). This script will set the channel on the econotag and then create a .pcap with the packets received.
Needs pyserial
apt-get install python-serial
pip install pyserial
./rftestrx2pcap.py tty chan [outfile]
rftestrx2pcap.py takes the tty/com port as the first argument and the 802.15.4 channel as the second (from 11 through 26). The third argument is an optional output file.
Dump packets to a file:
$ ./rftestrx2pcap.py /dev/ttyUSB1 26 > foo.pcap
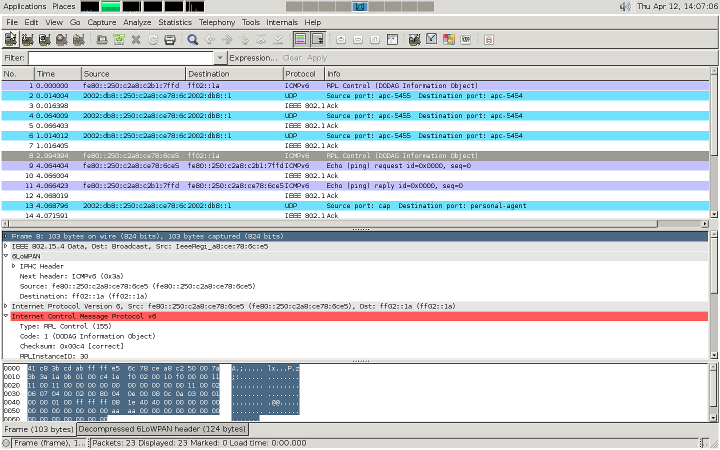
This .pcap can then be opened in wireshark.Alternatively for live captures, you can pipe directly into wireshark with:
$ ~/libmc1322x/tools/rftestrx2pcap.pl -t /dev/ttyUSB1 | wireshark -k -i -
For windows you can use the optional third argument to output to a .pcap:
$ ./rftestrx2pcap.py /dev/ttyUSB1 26 foo.pcap
© 2013 Mariano Alvira. Distributed under the GNU FDL v1.3 <script type="text/javascript"> var _gaq = _gaq || []; _gaq.push(['_setAccount', 'UA-9770084-1']); _gaq.push(['_trackPageview']); (function() { var ga = document.createElement('script'); ga.type = 'text/javascript'; ga.async = true; ga.src = ('https:' == document.location.protocol ? 'https://ssl' : 'http://www') + '.google-analytics.com/ga.js'; var s = document.getElementsByTagName('script')[0]; s.parentNode.insertBefore(ga, s); })(); </script>